What is malware (or malicious software)? Malware is any computer program or software that is designed for nefarious purposes. Malware is used to steal data or inflict damage on computer or software systems. Malware includes various types of cyber threats such as viruses, adware, spyware, and ransomware. Most often, the goal of cyber attacks is to use the malware for financial gain.
Using devious social engineering tactics such as phishing, cyber criminals can gain illicit access to a corporate network. Once inside the network they can move around at will, steal data and intellectual property, access confidential information, spy, and damage systems.

What Is the Intent of Malware?
The motives behind the perpetrators of malware are many but they have one thing in common–malware is intended to reward the perpetrator at the victim’s expense. For example, in digital environments cyber criminals use harmful software, a.k.a. malware, to steal financial assets, and encrypt business critical data or lock up computing systems, for ransom.
Nation states engaged in espionage use malware to steal intellectual property and intelligence data from adversaries or competitors, or to sabotage infrastructure such as municipal power systems to cut internet communications or cause major disruptions in service. Here are a few reasons why bad actors use malware to perpetrate cyber attacks:
- financial gain
- data theft
- system disruption
- espionage
- sabotage
Different Types of Malware
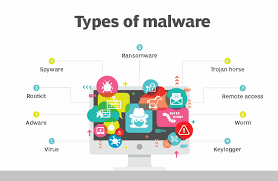
Here are the different types of malware :
1. Viruses
Viruses are perhaps one of the most well-known malware types. A computer virus links its malicious code with clean code and waits for a user to execute it. Viruses spread quickly through a variety of systems, affecting how they work. They also corrupt website content files and prevent users from accessing their computers. They are often hidden inside an executable file.
2. Worms
Worms are one of the more common malware types. A worm moves through a network by forming connections with one machine after another. In this manner, they move between connected computers and can quickly exploit the whole network if not stopped.
3. Trojan viruses
Trojans are named after the Trojan horse from Greek mythology. Similar to Greek soldiers hiding inside an apparently innocent structure, Trojans appear to be legitimate software. Because they seem innocent, they are accepted into the user’s computer. There, they create backdoors, allowing other advanced malicious software to gain remote access to the
4. Spyware
Spyware keeps track of what a user does on their computer. Even though spyware may not overtly damage your system, it still fits the malware definition. Spyware hides, like a spy, in the background of a user’s computer, collecting information without the user’s knowledge. This may include sensitive data like credit card details and passwords.
5. Keyloggers
A keylogger has the ability to record the keystrokes a user makes on the keyboard. It can then store this information and send it to an attacker. The attacker can then use the data to figure out passwords, usernames, and payment details.
6. Crypto jacking
Crypto jacking involves using a computer or other devices to mine for cryptocurrencies. An attacker uses the computing power of the target’s device to solve the complicated equations needed to generate digital currencies.
7. Rogue software
Rogue software pretends to offer targets help with getting rid of viruses and other kinds of malware. It then coerces them into inadvertently installing—and paying for—malware.
8. Scareware
Scareware uses social engineering to frighten or shock a user into thinking their system is vulnerable to an attack or potential hacking. However, no danger has actually been detected— it is a scam. The attacker succeeds when the user purchases unwanted—and dangerous—software in an attempt to remove or eliminate the “threat.”
Methods of Malware Attacks

In the section above, we identified the various types of malware along with the method by which they spread. The ways that malware can infiltrate and spread through networks continues to expand along with the threat vectors in the digital landscape, including the following:
- Unsecure devices that access the network such as personal mobile devices, PCs, and IoT devices open an attack vector for malware.
- Unsecure networks that are part of a supply chain or unsecure third-party partners’ networks, can infect the networks of other suppliers or give malware access to the enterprise network.
- Older devices on the network with software that is not routinely updated can become compromised and spread malware.
- Email attachments containing malicious code can be opened and forwarded to other users, spreading the malware across the enterprise.
- Phishing or spear phishing emails trick the recipient into sharing passwords that give access to the corporate network where malware can spread.
- Smishing texts, similar to phishing emails but on mobile phones, trick distracted users into clicking on malware links and entering personal or business credentials that enable malware to spread on the network.
- File servers, such as those based on the common internet file system or network file system can spread malware as users download infected files.
- File-sharing software can allow malware to replicate itself onto removable media such as thumb drives and then on to computer systems and networks.
- Peer to peer (P2P) file sharing can introduce malware by sharing infected files as seemingly harmless as video, music, or images,
- Remotely exploitable network vulnerabilities can enable a hacker to access systems regardless of geographic location
Malware Detection and Prevention
Once you have identified malware, you need to know how to find it. Much like a PC antivirus program and firewall, IT security experts can detect malware on a corporate network using enterprise cyber security solutions. These include intrusion prevention systems (IPS), next-generation firewalls, and sandboxing systems, which allow IT to attract and then study attacks.
Some malware, such as ransomware, reveals itself through its attack methods because it starts encrypting files and follows up with a ransom message. Other malware uses more subtle tactics, such as installing itself on the target system which paves the way for a hacker to access it later. To detect this kind of “backdoor” malware, your best bet is to use traffic filtering systems that can detect malicious software by examining the profiles of known threats or the behavior patterns of malicious software.
With today’s digitally enabled, work-from-anywhere business models, secure networking is more important than ever before. Therefore, solutions like Zero-Trust Network Access (ZTNA), Cloud Access Security Broker (CASB), Secure SD-WAN, all components of Fortinet Secure Access Service Edge (SASE) can help prevent cyber attacks by controlling authentication and authorization.
In this way, it’s possible to automate and control which users and devices can access what segment(s) of the network, and what systems and apps, specifically, they can use–whether on premises or remote.
How to Protect Against Malware Attacks?
It is important to be proactive when trying to avoid having malware infected systems in your organization. This involves a combination of prevention, mitigation, and education.
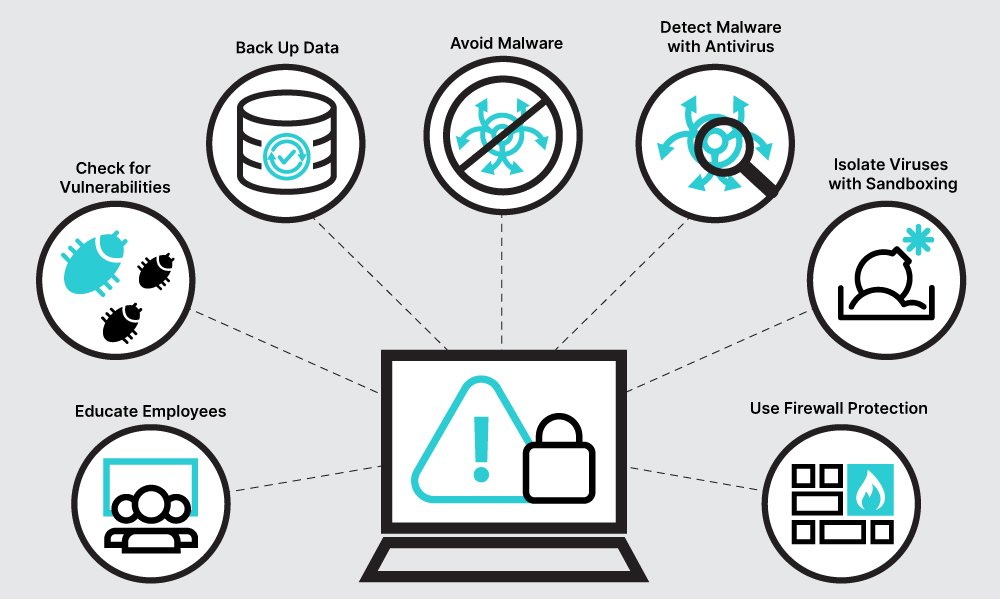
1. Avoid malware
Most malware is relatively easy to spot if you know the signs. The most common places to encounter it are within spam emails, malicious websites, and pop-ups that appear on your device either while using the internet or in the course of normal operation.
Phishing schemes that seek to trick users to disclose sensitive data could also use malware so that even if you do not provide the information the phisher needs, you still end up clicking something that gives them access to your system. Therefore, it is a good idea to never click on anything that appears randomly on your screen or open anything in an email—attachment or otherwise—that seems suspicious.
2. Back up data
Backing up data is a form of mitigation that will be invaluable if a malware attack is successful. All endpoints and servers should have backups that are shielded from malware. If an attack is successful, you can use the backup to restore your infected device after wiping it.
3. Educate employees
All employees should have a working understanding of what malware is, how it penetrates a system, its harmful effects, and tips for how to best avoid it. This may include arming them with preventative knowledge such as the value of multi-factor authentication (MFA) and developing strong passwords. Employees should also know to look for red flags in an email or pop-up, as well as who to notify and what to do—or not do—if they suspect their endpoint has been exposed.
4. Check for vulnerabilities
Have a full cybersecurity system that can help you find the places where malware might enter your network. A proactive security system can closely monitor all endpoints (including mobile devices) as well as a variety of servers—both on-premises and in the cloud.
5. Isolate viruses with sandboxing
Sandboxing can block a malware attack by isolating and confining malware—such as a malicious email attachment—to a protected environment. Inside a sandboxed area, the IT team can observe how the malware behaves and how it reacts to security measures taken to neutralize it. All the while, other devices and sections of the network are protected from infection. You can control and isolate malicious software with Forti Sandbox.
6. Use firewall protection
Firewall technology prevents malware delivery by filtering network traffic. This includes traffic entering and exiting the network. Two-way malware protection is important because malicious programs within your system can be leveraged to affect users, devices, and networks that connect to yours. NGFWs incorporate packet filtering, network monitoring, Internet Protocol (IP) mapping, IP security (IPsec), and secure sockets layer virtual private network (SSL VPN) support. It also uses deeper inspection measures to protect a company from intrusion or from having applications hijacked.
7. Detect malware with antivirus
The Forti Guard Antivirus Security Service leverages the power of the Forti Guard Labs Global Threat Intelligence system. In the span of a minute, Forti Guard eliminates, on average, 95,000 malware programs for real-time protection. Forti Guard does this by incorporating knowledge of the different types of malware within the global threat landscape. Countermeasures are engineered to neutralize each type of threat, and then they are automatically enacted by Forti Guard, thereby protecting the networks under the Forti Guard umbrella.
The Forti Guard Antivirus can attach to FortiGate, Forti Sandbox, Forti Mail, Forti Web, and Forti Client.
8. Malware removal
The best way to remove malware from an infected computer or personal device is by running antivirus security software. Using data about each kind of threat, antivirus apps can detect, remove, and quarantine malware on the different devices you use: desktop, laptop, smartphone, or tablet. Antivirus programs use data from its most recent update to locate the widest possible range of threats, so it is best to choose a solution that constantly updates.
Effective Malware Removal Process
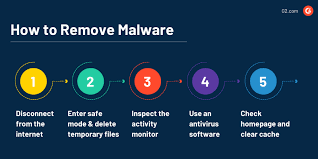
It’s important to remove malware from a computer or isolate it from network environments as soon as possible to mitigate damage. For enterprise workstations, malware removal can be done remotely with business antivirus tools. If the malware evades the antivirus software more sophisticated forms of removal might be necessary.
The steps for removing malware from an individual computer are similar whether the infected system is used for business or by a consumer. The process is as follows:
- Update the machine’s antivirus software and run an antivirus scan on the entire system. Before beginning a scan ensure the antivirus has not been disabled by the malware. Scans can take several minutes or longer to complete.
- Read the antivirus report to see what the scan discovered. Most antivirus software quarantines suspicious files and asks you what to do with them after the scan. Remove suspicious files.
- Reboot the computer. Check to make sure that your antivirus software is enabled and set to scan the computer every week. Scanning regularly on schedule ensures that malware is flagged if it installs again.
- Ensure that malware is completely removed. If you do not, it could be coded to re-infect a newly scanned and cleaned computer.
- If the malware is not removed you can reset the computer to factory settings and re-image the computer. If you have a complete backup of your operating system and files, re-imaging re-installs everything, including files, so that you can recover from your last storage point.
- If you don’t have a complete backup of your operating system and files, resetting will return the computer to the state it was when you first purchased it.
Rundown of the Biggest Insights Into Malware Facts
- A big problem: the average number of malware attacks worldwide annually is 5.4 billion.
- Malware (17%), phishing attacks (17%), and ransomware (19%) were the most common causes of cyberattacks in 2022.
- The number of detected malware has grown from 183 million in 2017 to nearly 493 million (in 2022) by some estimates.
- As recently as in 2022 trends show that these threats are becoming stealthier—such as increasing use of file less malware and also encrypted malicious files.
- Check all your connections for malware infection. Linux-based Internet of Things (IoT) devices saw a 35% increase in malware attacks in 2021 alone.
- Your mobile device may also be a target. Mobile malware on iPhone and Android devices has been on the rise in some regions.

1982
A plain and simple “unwanted software” is the most widely accepted malware definition, and the first example was Elk Cloner, which was spread through floppy disks to Apple II systems in 1982. While this didn’t necessarily harm computers, it represented an unwanted intrusion, fitting the malware meaning most people embrace.
1990s
Then, in the 1990s, because Windows was such a popular operating system for personal computers, hackers began writing code using the macro language used by the common application Microsoft Word. These spread across the vast ecosystem of Windows PCs, giving birth to the concept of a malware-dominated threat landscape.
2002
Between 2002 and 2007, with the advent of instant messages, attackers started developing worms—which can replicate on their own—and they infected computers through AOL, MSN Messenger, AIM, and Yahoo Messenger.
The message would entice recipients with a catchy lure, such as, “Who’s that with you in this pic???” When the target clicked on a link in the message, they would get malware downloaded on their system. The malware would then send links to every name on the victim’s contact list, effectively weaponizing their computer.
2005
Adware reared its annoying head from 2005 to 2009, starting out as legitimate software used to promote products. But as the ads drifted from somewhat true to fallacious, software publishers started suing adware producers for fraud. As a result, many shut down. But the full-screen, unclosable ad inherent in adware has survived until today.
2007
Social networks saw a boom in popularity from 2007 to 2009. Malware developers used Myspace, Twitter, and Facebook to propagate malicious links, applications, and advertisements.
2013
One of the most dangerous malware types arose in 2013: ransomware. It was spread using Trojans, which consist of malware hidden in apparently benevolent software, as well as exploits .Ransomware has continued as a prime malware attack vector to this day.
2015
In 2017, crypto jacking, which involves hackers using people’s devices to mine crypto, emerged, riding the wave of popularity still enjoyed by cryptocurrencies. Ransomware, crypto jacking, and adware are still trending in the malware sphere. There is no sign they will slow down anytime in the near future.
Challenges of Malware Detection and Mitigation

Malware, short for malicious software, continues to evolve rapidly, posing significant challenges to cybersecurity professionals. Here are some of the primary challenges associated with malware detection and mitigation:
1. Rapid Evolution and Polymorphism:
- New Variants: Malware authors constantly create new variants to evade detection by existing security solutions.
- Polymorphism: Malware can change its appearance or behavior to avoid detection, making it difficult to identify and block.
2. Zero-Day Threats:
- Unknown Malware: Zero-day attacks exploit vulnerabilities that are unknown to security vendors, making them difficult to detect and respond to.
- Rapid Exploitation: Attackers often exploit zero-day vulnerabilities quickly before patches become available.
3. Sophistication and Persistence:
- Advanced Techniques: Malware authors employ increasingly sophisticated techniques, such as rootkits, fileless attacks, and supply chain attacks.
- Persistence: Malware can persist on infected systems, making it difficult to eradicate completely.
4. Diverse Attack Vectors:
- Multiple Channels: Malware can be delivered through various channels, including email attachments, malicious websites, social media, and removable media.
- Targeted Attacks: Attackers may use targeted attacks to compromise specific organizations or individuals.
5. Detection Limitations:
- Evasion Techniques: Malware authors use techniques to evade detection by traditional antivirus and intrusion detection systems.
- False Positives and Negatives: Security solutions may incorrectly identify benign files as malicious (false positives) or fail to detect malicious files (false negatives).
6. Resource Constraints:
- Limited Budgets: Organizations may have limited budgets for cybersecurity, making it difficult to invest in the latest technologies and expertise.
- Overwhelmed Staff: Security teams may be overwhelmed by the volume of threats and lack the resources to respond effectively.
7. User Behavior and Awareness:
- Phishing Attacks: Users may be tricked into clicking on malicious links or opening attachments, leading to infections.
- Lack of Awareness: Users may not be aware of the latest threats or best practices for protecting themselves.
Addressing these challenges requires a multifaceted approach, including:
- Continuous Updates: Security solutions must be updated regularly to address new threats.
- Behavior-Based Detection: Using techniques that analyze the behavior of software to identify malicious activity.
- Threat Intelligence: Sharing information about threats and attacks to improve detection and response.
- User Education: Training users to recognize and avoid phishing attacks and other threats.
- Incident Response Planning: Having a plan in place to respond to security incidents effectively.
Best Practices of Malware
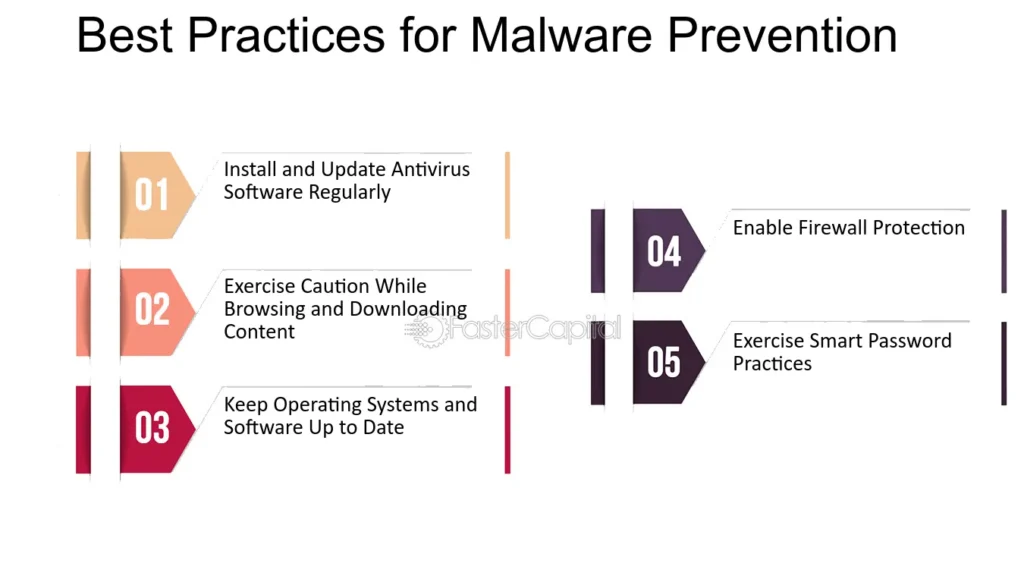
Here are some best practices to help protect your systems from malware:
1. Keep Software Updated:
- Patches and Updates: Regularly install updates for operating systems, applications, and firmware to address known vulnerabilities.
- Automatic Updates: Enable automatic updates to ensure timely application of security patches.
2. Use Strong Passwords:
- Complex Passwords: Create strong, unique passwords that are difficult to guess or crack.
- Password Managers: Consider using a password manager to securely store and manage complex passwords.
3. Be Cautious of Email Attachments:
- Unknown Senders: Avoid opening email attachments from unknown or suspicious senders.
- Verify Content: Before opening an attachment, verify the sender’s identity and the legitimacy of the content.
4. Avoid Phishing Attempts:
- Suspicious Links: Be wary of clicking on links in emails or messages that seem suspicious or unexpected.
- Verify Websites: Double-check the URL of websites before entering sensitive information.
5. Practice Safe Browsing:
- Reputable Websites: Limit browsing to reputable websites and avoid visiting suspicious or malicious sites.
- Browser Extensions: Use browser extensions that can help identify and block malicious websites.
Conclusion
The battle against malware is a complex and ongoing challenge. While technological advancements and security measures play a vital role, the human element remains a critical factor. By staying informed, practicing safe computing habits, and utilizing effective security solutions, individuals and organizations can better protect themselves from the ever-evolving threat of malware.
Malware, a term encompassing malicious software designed to harm computer systems, has been a persistent threat for decades. Despite significant advancements in cybersecurity technology, the landscape of malware continues to evolve, presenting new challenges for individuals and organizations.
FAQs
Malware refers to the various types of malicious software, such as viruses, spyware, and ransomware. Cyber-criminals can use these tools to gain access to a network and its devices to steal data or damage systems.
Here are the different types of mobile malware that may impact your online network or attached devices.
1.Viruses
2.Worms
3.Trojan viruses
4.Spyware
5.Ransomware
The best way to remove malware from an infected computer or personal device is by running antivirus security software. Using data about each kind of threat, antivirus apps can detect, remove, and quarantine malware on the different devices you use: desktop, laptop, smartphone, or tablet.
