Incident response is the strategic, organized response an organization uses following a cyberattack. The response is executed according to planned procedures that seek to limit damage and repair breached vulnerabilities in systems.
IT professionals use incident response plans to manage security incidents. Having a clearly defined incident response plan can limit attack damage, lower costs, and save time after a security breach.
A cyberattack or data breach can cause huge damage to an organization, potentially affecting its customers, brand value, intellectual property, and time and resources. Incident response aims to reduce the damage an attack causes and help the organization recover as quickly as possible.

Why Incident Response Planning Is Important
Cyberattacks can have a damaging effect on brand reputation, leading to an organization losing customers and suffering huge fines. Having a response plan in place and taking action based on the findings is vital to learning lessons and avoiding stringent punishments for suffering data loss. Incident response planning is a critical component of cybersecurity strategy. It outlines a structured approach to handling security breaches, data leaks, and other cyber incidents. Here’s why it’s so important:
1. Minimizing Damage:
- Swift Response: A well-crafted plan ensures a rapid response to incidents, limiting the potential damage to systems, data, and reputation.
- Damage Control: Effective response procedures can help contain the spread of malware, prevent further data breaches, and mitigate financial losses.
2. Regulatory Compliance:
- Mandatory Requirements: Many industries and regions have strict data protection regulations (like GDPR, CCPA, HIPAA) that require organizations to have incident response plans in place.
- Avoiding Penalties: Non-compliance can result in hefty fines and legal consequences.
3. Reputation Management:
- Trust and Confidence: A timely and effective response to a security incident can help maintain customer trust and confidence.
- Crisis Communication: A well-defined plan outlines how to communicate with stakeholders, media, and customers during a crisis.
4. Business Continuity:
- Resumption of Operations: A robust incident response plan helps ensure that critical business functions can be restored quickly after an attack.
- Disaster Recovery: It complements disaster recovery plans by addressing specific security threats and incidents.
5. Proactive Security:
- Identifying Vulnerabilities: The process of creating an incident response plan can highlight potential vulnerabilities in your systems and security measures.
- Continuous Improvement: Regular review and updates of the plan help maintain a proactive security posture.
CSIRT: Computer Security Incident Response Team
A Computer Security Incident Response Team (CSIRT) is a group of individuals responsible for handling and mitigating security breaches within an organization. They are trained to respond to cyberattacks, data breaches, and other security incidents in a timely and effective manner.
Key Responsibilities of a CSIRT:
- Incident Detection and Response: Identifying and responding to security incidents, such as malware infections, unauthorized access, and data breaches.
- Threat Analysis: Analysing threats and vulnerabilities to understand the nature and scope of security incidents.
- Incident Containment: Isolating affected systems or networks to prevent further damage.
- Root Cause Analysis: Investigating the root cause of incidents to prevent future occurrences.
- Forensics: Collecting and analysing digital evidence to identify the source of attacks and gather information for legal or investigative purposes.
- Communication and Coordination: Communicating with stakeholders, including management, legal counsel, and law enforcement, as needed.
- Incident Reporting: Documenting incidents and providing reports to management and relevant authorities.
- Training and Awareness: Conducting security awareness training for employees to help prevent incidents.
Benefits of Having a CSIRT:
- Reduced Risk: A CSIRT can help reduce the risk of data breaches and other security incidents.
- Faster Response: A well-trained CSIRT can respond to incidents more quickly and effectively.
- Improved Security Posture: A CSIRT can help improve an organization’s overall security posture.
- Compliance: A CSIRT can help organizations comply with industry regulations and standards.
6 Steps Of An Incident Response Plan
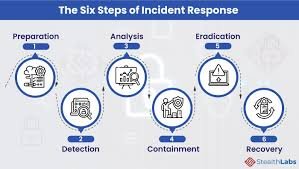
The incident response steps that organizations need to take have been summarized in a six-step plan by the SANS Institute. The Incident Handler’s Handbook outlines the basic foundation for businesses to create their own incident response policies, standards, and teams.
1. Preparation and Planning:
- Identify Critical Assets: Determine the most valuable assets to protect, such as data, systems, and applications.
- Develop Response Teams: Assemble teams with the necessary skills and expertise to handle different types of incidents.
- Create Communication Channels: Establish clear communication channels for internal and external stakeholders.
- Conduct Training: Provide training to team members on incident response procedures and tools.
2. Detection and Analysis:
- Implement Monitoring: Use monitoring tools to detect unusual activity or potential threats.
- Analyze Logs: Review logs and system data to identify the nature and scope of the incident.
- Gather Evidence: Collect digital evidence to support investigations and legal proceedings.
3. Containment:
- Isolate Affected Systems: Isolate compromised systems or networks to prevent further damage.
- Disable Access: Disable access to affected accounts or resources.
- Implement Temporary Measures: Implement temporary security measures to mitigate the impact of the incident.
4. Eradication:
- Remove Malware: Remove any malware or malicious code from affected systems.
- Restore Systems: Restore systems to a clean state using backups or recovery procedures.
- Patch Vulnerabilities: Apply security patches to address known vulnerabilities.
5. Recovery:
- Restore Operations: Restore critical business functions and operations.
- Review and Update Plans: Review and update the incident response plan based on lessons learned.
- Communicate with Stakeholders: Communicate with stakeholders, including customers, employees, and partners, about the incident and its resolution.
6. Lessons Learned:
- Conduct Post-Incident Review: Conduct a thorough review of the incident to identify areas for improvement.
- Update Response Plan: Update the incident response plan to address any weaknesses or gaps identified in the review.
- Provide Training: Provide additional training to team members based on the lessons learned.
What Is an Incident Response Plan?
An incident response plan is a document that details the security processes to be carried out in case of an incident, and those responsible for incident response. An incident response plan typically includes the following details:
- Incident response methods and strategies
- How incident response can support your organization’s broader mission
- Activities required for each stage of incident response
- Roles and responsibilities for completing incident response activities
- Communication channels between the incident response team and the rest of the organization
- Metrics for evaluating the efficiency of incident response
The benefits of an incident response plan don’t end when a cybersecurity incident is resolved. The plan continues to provide support for litigation, documentation to submit to auditors, and historical knowledge that enables a better response to similar incidents in the future.
Incident Response Steps

A standard incident response plan that may be implemented by an organization includes the following steps:
Step 1: Early detection
A security event occurs, and the system detects it. Typically, the security information and event management (SIEM) platform alerts the incident response team.
Step 2: Analysis
Analysts review alerts, identify indicators of compromise (IoC), and use them to triage the threat. They will often perform additional testing, reviewing related alerts and ruling out false positives to get a complete picture of suspicious events.
Step 3: Prioritization
Analysts need to understand the impact of security incidents on the organization’s business activity and valuable assets. Prioritizing incidents helps a team understand which security events to focus on, and how to best manage resources in subsequent steps.
Step 4: Notification
First, the incident responder notifies the appropriate people within the organization. In case of a confirmed breach, organizations typically notify external parties, such as customers, business partners, regulators, law enforcement agencies, or the public. The decision to notify external parties is usually left to senior management.
Step 5: Containment and forensics
Incident responders take action to stop the incident and prevent the threat from reinfecting the environment. They also collect forensic evidence as needed for further investigation or future legal proceedings.
Step 6: Recovery
Incident responders eradicate malware from affected systems, then rebuild, restore from backup, and patch those systems to restore normal operation.
Step 7: Incident review
To prevent an incident from reoccurring and to improve future response, security personnel review the steps that led to the detection of the most recent incident. They identify aspects of successful incident response, opportunities to improve systems (such as tools, processes, and staff training), and recommend remediations for discovered vulnerabilities.
Incident Response Frameworks
Some large organizations with significant security expertise have developed incident response frameworks to help organizations create standardized response plans. The National Institute of Standards and Technology (NIST) and the Sys Admin, Auditing, Networking, and Security Institute (SANS) have each developed well-known incident response frameworks.
Incident Response Plan Templates
Developing an incident response plan can be difficult. Using one of the following templates provides structure and direction for this task:
- National Cyber Security Centre (NCSC) Planning guide—the NCSC is a key cybersecurity organization that provides cybersecurity assistance to major UK organizations.
- Sysnet’s Incident Response Template—this template outlines how to identify security incidents, the roles and responsibilities of key stakeholders and incident response planners, and the different types of incidents to consider.
- Incidentresponse.com—this site offers several playbooks for scenarios such as malware, phishing, and unauthorized access, all mapped to the NIST Incident Response Framework. These manuals are stand-alone documents separate from an incident response plan but should be referenced during its creation (learn more about incident response playbooks in the following section).
Incident Response Playbooks
An incident response playbook provides teams with standard steps and procedures for responding to and resolving incidents in real time. Playbooks can also include peacetime training and exercises to prepare the team for the next event.
Playbooks are an integral part of DevOps and IT Ops incident management and cybersecurity. They help teams handle unplanned outages and restore systems to order, and their organizational policies and practices ensure a consistent response to incidents and security threats.
A playbook typically contains the following elements:
- Runbooks
- Checklists
- Templates
- Training exercises
- Security attack scenarios
- Simulation drills
Incident Response Team

Incident response teams are groups of IT professionals who prepare for and respond to cyber attacks. An incident response team’s responsibilities include developing a proactive incident response plan, testing and resolving system vulnerabilities, maintaining strong security best practices, and providing support for all incident handling actions.
Incident response team members typically have varied skills, backgrounds, and roles, so they can prepare for a range of security incidents.
The specific skill set of organizations’ incident response teams may differ because companies have different personal risk profiles and business processes. In general, the core functions of incident response team members are:
- Leadership—coordinate the overall direction and strategy of response activities, freeing the rest of the team to focus on minimizing damage, recovering quickly, and operating efficiently.
- Investigation—coordinate efforts to determine the root cause of an incident, which helps to eradicate current threats and prevent future ones. To do so, it is important to gather as much relevant information as possible.
- Communications—manage relevant internal and external communications required for incident response. Communication may be required between teams and departments within an organization or with external stakeholders.
- Documentation—record incident response actions and activities.
- Legal representation—protect the organization by ensuring that incident response activities comply with laws and regulations.
A Framework for Leveraging Incident Response Tools
In addition to seeking administrative support and following a documented incident response plan, incident response tools are key to preparing for and responding to security incidents. Cybersecurity tools should be implemented long before an incident occurs, because they can provide critical information that can be used to detect, investigate, and respond to incidents.
Most organizations already have common security controls in place to support incident response capabilities, particularly with regard to logging and alerting. However, there are dedicated tools that can guide a team through its incident response workflow and provide all the details needed to make an informed decision.
Some organizations follow the Observe, Orient, Decide, Act (OODA) cycle to provide guidance on which tools are needed and when. This military approach to incident response follows a four-step approach to threats:
- Assess visibility of network traffic, operating system, and applications – establish a baseline for the organization’s environment and provides real-time information about what happened before, during, and after a security incident.
- Collect contextual information – gather detailed contextual information and intelligence about existing threats and running attacks.
- Collect real-time and forensic information – gather information about active, currently occurring threats and anomalous behaviors (as well as performing reactive, post-event research) to help security teams make informed decisions about how to respond.
- Address the threat – take steps to resolve the threat, minimize risk and business impact, and return to normal operations.
Incident Response Tool
Security Orchestration, Automation, and Response
SOAR refers to platforms that offer tools for collecting security data from various sources. A SOAR solution may combine machine learning and human input to analyze the data to extract insights and prioritize the relevant incident response procedures.
SOAR software typically includes three capabilities:
- Threat and vulnerability management
- Incident response
- Security operations automation
- Organizations use SOAR to collect and make sense of threat-related data from diverse sources, enabling automated threat responses.
User and Entity Behaviour Analytics
UEBA solutions use large datasets and machine learning to establish baselines for typical behavioural patterns, allowing them to identify atypical behaviour within the network, which may indicate threats. The emphasis on suspicious behaviour allows UEBA to detect threats that can evade traditional security and antivirus tools, including non-malware-based attacks.
Security Information and Event Management
SIEM is a security management approach that provides a unified system to combine information and event management functions. SIEM solutions deploy multiple data collection agents to hierarchically collect event data from servers, end-user devices, and network infrastructure. A central management console consolidates the data, allowing security analysts to filter the noise and prioritize real security incidents.
Endpoint Detection and Response
EDR systems collect and analyze endpoint security data to protect the network from vulnerable user devices and workstations. EDR aims to detect security breaches in real time, enabling rapid response. This approach helps identify emerging and advanced threats that traditional security tools might not. The specific capabilities of each EDR solution may vary significantly.
Extended Detection and Response
XDR solutions are SaaS tools for detecting security threats and implementing incident response procedures. XDR tools integrate several security capabilities in a unified security operations solution, making sophisticated incident response capabilities more accessible and affordable.
The advantage of XDR is its consolidation of multiple security products building on EDR capabilities. It can improve the productivity of security operations with enhanced detection and response and centralized visibility and control across enterprise environments. XDR tools ingest and distill multiple telemetry streams and analyse threat vectors and tactics. They help speed up response efforts by handling the detection and investigation processes.
Incident Response Services
Incident response is most effective when undertaken quickly by experienced responders. Organizations often lack the resources to maintain a full incident response team that is active 24 hours a day. One option is to work with an external organization that provides professional incident response services.
Engaging with these organizations provides the following benefits:
- Availability—the sooner the incident response team gets to work, the lower the cost and the lower the impact of an attack on the organization. Cybersecurity incidents can occur at any time, and it can be difficult to reach incident response team members outside of business hours. Professional incident response providers have multiple teams of staff to provide better coverage and higher availability.
- Experience—mishandling security incidents can increase costs and damage an organization. For example, a ransomware attack can destabilize an infected system, which means that encrypted data may not be recovered upon reboot. Professional incident responders have the experience needed to handle such security incidents efficiently and accurately.
- Specialized expertise—incident response often requires expertise in areas such as forensic analysis and malware reverse engineering. While most companies won’t need to have these skills in-house, a dedicated incident response team has access to the experts they need to handle cybersecurity incidents properly.
- Managing the entire incident response process—outsourced incident response providers should support all of the organization’s incident response needs. This includes preparing for incident response, managing detected intrusions, and mitigating future attacks.
Challenges of Incident Response

Incident response can be a complex and challenging process, even for well-prepared organizations. Here are some of the common challenges faced:
1. Detection Delays:
- Hidden Threats: Many threats, especially advanced persistent threats (APTs), can remain undetected for extended periods.
- Insufficient Monitoring: Inadequate monitoring tools or processes can delay the discovery of incidents.
2. Limited Resources:
- Understaffed Teams: Incident response teams may be understaffed or lack the necessary skills and expertise.
- Budget Constraints: Organizations may face budget limitations that hinder their ability to invest in adequate security measures.
3. Complex Environments:
- Hybrid Infrastructures: Modern IT environments often include a mix of on-premises, cloud, and hybrid systems, making incident response more challenging.
- Third-Party Dependencies: Relying on third-party vendors can introduce additional complexities and risks.
4. Regulatory Compliance:
- Strict Requirements: Organizations must comply with various data protection regulations, which can increase the pressure to respond to incidents quickly and effectively.
- Fines and Penalties: Non-compliance can result in significant fines and legal consequences.
5. Supply Chain Attacks:
- Indirect Impact: Attacks on third-party suppliers or vendors can have a significant impact on an organization’s security.
- Complexity of Investigation: Investigating supply chain attacks can be complex and time-consuming.
6. Evolving Threats:
- New Attack Techniques: Cybercriminals are constantly developing new attack techniques, making it difficult to stay ahead of the curve.
- Emerging Technologies: New technologies, such as artificial intelligence and machine learning, can introduce new security challenges.
7. Human Error:
- Mistakes and Oversights: Human error can contribute to incidents, such as accidentally clicking on malicious links or misconfiguring systems.
- Lack of Awareness: Employees may not be aware of the latest security threats or best practices.
8. Data Privacy Concerns:
- Sensitive Information: Incident response teams must handle sensitive data with care to protect privacy and comply with regulations.
- Public Relations: Data breaches can have a significant impact on an organization’s reputation, making it essential to handle incidents with transparency and sensitivity.
Conclusion
The conclusion of an incident response process involves several critical steps to ensure the organization is fully recovered and protected from future threats. Here’s a breakdown of the key components:
1. Lessons Learned Analysis:
- Review the incident: Conduct a detailed review of the incident to understand what went right, what went wrong, and identify any root causes.
- Identify areas for improvement: Determine where processes, procedures, or technologies can be strengthened to prevent similar incidents in the future.
- Document findings: Create a comprehensive report documenting the incident, its impact, and the lessons learned.
2. Incident Response Plan Updates:
- Revise and update: Modify the organization’s incident response plan based on the insights gained from the incident.
- Incorporate new best practices: Incorporate any new security best practices or technologies that can enhance incident response capabilities.
- Test and validate: Conduct regular testing and validation of the updated plan to ensure its effectiveness.
3. Security Posture Enhancement:
- Implement recommended changes: Implement any recommended changes to improve the organization’s overall security posture, such as strengthening access controls, patching vulnerabilities, or enhancing monitoring capabilities.
- Review and update security policies: Ensure that security policies and procedures align with the lessons learned and updated incident response plan.
FAQs
Incident response is a plan used following a cyberattack. IT professionals use it to respond to security incidents.
Incident response aims to reduce the damage an attack causes and help the organization recover as quickly as possible.
Incident response is crucial for minimizing damage, maintaining compliance, managing reputation, ensuring business continuity, and identifying vulnerabilities.
