DLP, or Data Loss Prevention, is a cybersecurity solution that detects and prevents data breaches. Since it blocks extraction of sensitive data, organizations use it for internal security and regulatory compliance.
DLP enables businesses to detect data loss, as well as prevent the illicit transfer of data outside the organization and the unwanted destruction of sensitive or personally identifiable data (PII). It is also used to help organizations with data security and ensure they comply with regulations like the California Consumer Privacy Act (CCPA), EU General Data Protection Regulation (GDPR), and Health Insurance Portability and Accountability Act (HIPAA).The terms “data loss” and “data leakage prevention” are often used interchangeably, but DLP security enables organizations to defend themselves against both. DLP allows businesses to:
- Identify sensitive information across multiple on-premises and cloud-based systems
- Prevent the accidental sharing of data
- Monitor and protect data
- Educate users on how to stay complain.
Why is DLP important?
A DLP solution is essential to your risk reduction strategy, especially when it comes to securing endpoints like mobile devices, desktop computers, and servers.
Information security (InfoSec) refers to the security procedures that protect sensitive information from misuse, unauthorized access, disruption, or destruction, including both physical and digital security. Key elements of InfoSec include the following:
Infrastructure and cloud security. Security for your hardware and software systems to help prevent unauthorized access and data leaks from your public cloud, private cloud, hybrid cloud, and multi cloud environments.
Cryptography. Algorithm-based communication security to ensure that only the intended recipients of a message can decipher and view it.
Incident response. How your organization responds to, remediates, and manages the aftermath of a cyberattack, data breach, or another disruptive event.
Disaster recovery. A plan for re-establishing your technological systems after a natural disaster, cyberattack, or other disruptive events.
Why You Need DLP
The threat of data breaches—incidents where protected is stolen, used, or viewed by an unauthorized individual—has rapidly increased as the world became more digital. There were more than 3,800 breaches in the first half of 2019 alone. DLP is a crucial tool in helping businesses protect their data.
Personally identifiable information (PII)
PII is data that could potentially identify an individual or distinguish them from another person. This includes end-users’ email addresses, mailing addresses, and Social Security numbers, as well as IP addresses, login IDs, social media posts, and biometric and geolocation information. There are stringent regulations in place to protect this, such as GDPR, that grant people more rights around how companies handle their data and impose heavy fines for noncompliance and breaches.
DLP security enables businesses to classify, identify, and tag data and monitor activities and events surrounding it. It also provides the reporting capabilities that let organizations complete compliance audits.
Intellectual property (IP)
Intellectual property includes software, proprietary data, and original works. IP owners need to ensure their digital assets are secure behind proper security protocols and defenses, including firewalls, restricted access privileges, and intrusion detection and prevention systems.
Malicious actors who gain access to intellectual property may cause severe losses by destroying irreplaceable information or code, copying protected assets and selling or distributing them on the Internet, and otherwise exploiting unauthorized access for their own gain.
HIPAA compliance
HIPAA places extensive data security requirements on all businesses that have access to, process, and store any protected health information. The organization defines guidelines, policies, and procedures for maintaining the privacy and security of individually identifiable health information. It also outlines offenses and civil and criminal penalties for failing to protect this data.
Like GDPR, DLP is vital for organizations that need to comply with HIPAA. It allows them to identify, classify, and tag data that is covered by regulations and ensure end-users are protected.
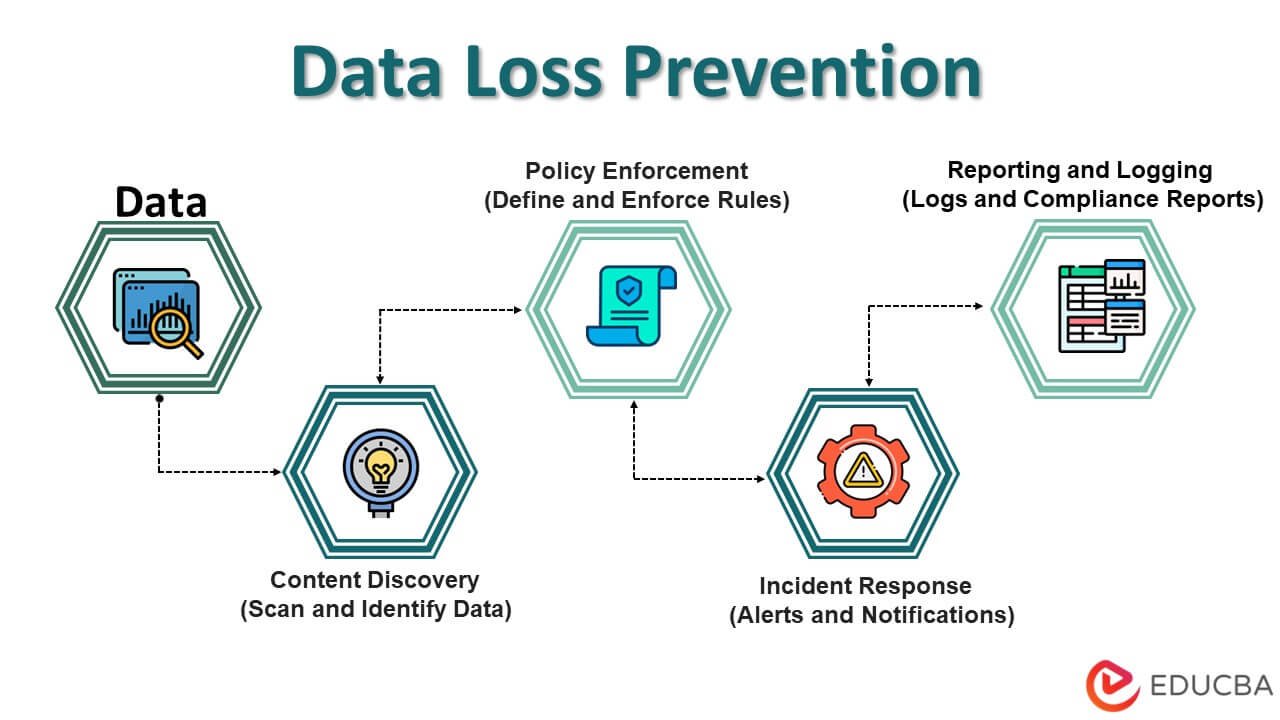
How DLP Works
DLP systems protect businesses’ data by identifying sensitive information, then using deep content analysis to detect and prevent potential data leaks. This content analysis uses methods like keyword matches, regular expressions, and internal functions to recognize content that matches a company’s DLP policy. As a result, businesses can identify, monitor, and automatically prevent the theft or exposure of protected data.
Define sensitive data
The first step in deploying DLP is for businesses to define the sensitive data they want to protect and build a DLP policy around. This could be credit card details, email addresses, and Social Security numbers, or simply a list of names in a spreadsheet.
A DLP policy contains:
- Locations and systems where data needs to be protected
- When and how to protect data
- Rules that define sensitive data and actions when a security risk is discovered
- Conditions that assign different actions to different risk levels
Take a proactive approach
Simply having a DLP solution in place is not enough to keep attackers at bay. Businesses need to monitor user activity and protect confidential data when it is at rest, in use, and in motion. Data in motion also referred to as data in transit, this is data that is actively moving from one location to another, either over the internet, between networks, from a local storage device to the cloud, or through a private network. Data can often be less secure while in motion, so it is vital to have effective data protection measures in place.
Detect and respond in real-time
DLP uses several methods to detect sensitive data, but the most common is regular expression pattern. This analyzes content for common patterns, such as 16-digit card numbers or nine-digit Social Security numbers, alongside indicators like the proximity of certain keywords.
For example, a Visa card has 16 digits, but not every 16-digit number will be a credit card number. So DLP performs a checksum calculation to confirm whether the numbers match the patterns of various brands. It also looks for the existence of keywords like “VISA” or “AMEX” in proximity to dates that could be an expiration date to decide whether sensitive information is at risk.
When a violation is discovered, DLP remediates it by sending alerts, encrypting data, and other actions that prevent users from accidentally or maliciously sharing sensitive information. It also provides reports that enables businesses to meet compliance and auditing requirements, as well as identify areas of weakness.
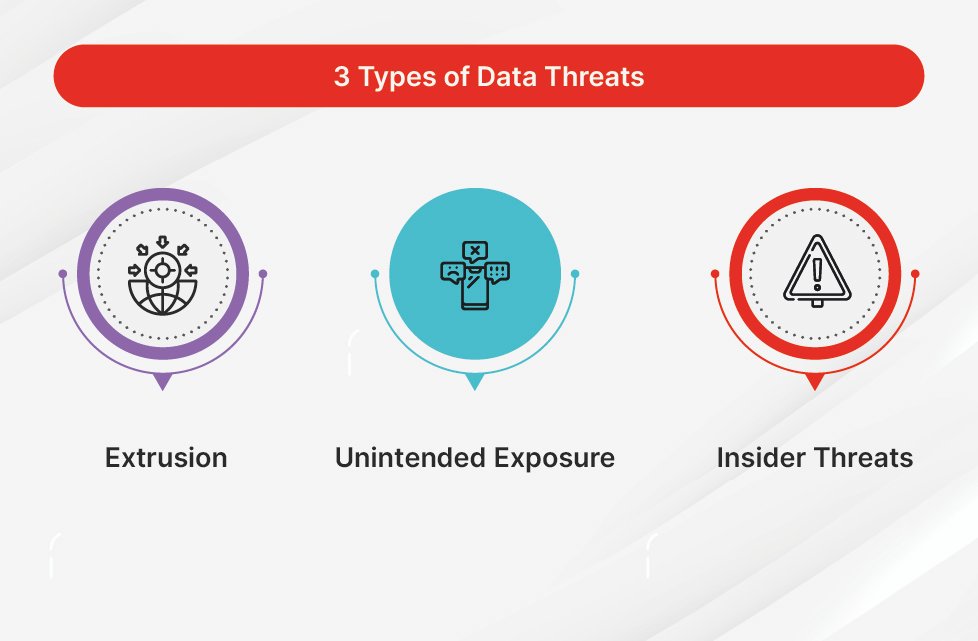
Types of Data Threats
Cybercriminals deploy a wide range of hacking methods that range in simplicity and sophistication. Common types of data threats include:
Extrusion
Extrusion is the act of cybercriminals targeting and attempting to steal sensitive data. They try to penetrate businesses’ security perimeters using techniques like code injection, malware, and phishing.
Wanna Cry was dubbed the biggest malware attack in history after it infected 230,000 computers in 150 countries in May 2017. Attackers targeted a vulnerability in older versions of Windows, then encrypted files and demanded a ransom fee in exchange for unlocking them.
Unintended exposure
Breaches can also be caused by unintended or negligent data exposure. This typically occurs as a result of inadequate employee data procedures, in which employees either lose sensitive information or provide open access to their account or data. It can also be caused by businesses not putting appropriate access restrictions in place on organizational policies.
A breach of cybersecurity firm RSA in 2011 compromised 40 million employee records after users clicked on emails sent from targeted phishing attacks. The attack came from two hacker groups within a foreign government pretending to be trusted colleagues. When employees clicked on the emails, the hackers gained access to systems and compromised SecurID authentication tokens.
Causes of Data Leaks
Three common causes of data leaks are:
- Insider threats — a malicious insider, or an attacker who has compromised a privileged user account, abuses their permissions and attempts to move data outside the organization.
- Extrusion by attackers — many cyber attacks have sensitive data as their target. Attackers penetrate the security perimeter using techniques like phishing, malware or code injection, and gain access to sensitive data.
- Unintentional or negligent data exposure — many data leaks occur as a result of employees who lose sensitive data in public, provide open Internet access to data, or fail to restrict access per organizational policies.
Data Leakage Prevention
You can use standard security tools to defend against data loss and leakage. For example, an Intrusion Detection System (IDS) can alert about attacker attempts to access to sensitive data. Antivirus software can prevent attackers from compromising sensitive systems. A firewall can block access from any unauthorized party to systems storing sensitive data.
If you are part of a large organization, you might turn to designated DLP tools or solutions to safeguard your data. You can also use tooling in the Security Operations Centre (SOC) to assist with DLP. For example, you can use a Security Information and Event (SIEM) system to detect and correlate events which might constitute a data leak.
Components of a Data Loss Solution
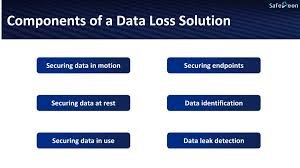
- Securing data in motion — technology installed at the network edge can analyze traffic to detect sensitive data sent in violation of security policies.
- Securing endpoints — endpoint-based agents can control information transfer between users, groups of users, and external parties. Some endpoint-based systems can block attempted communications in real time and provide user feedback.
- Securing data at rest — access control, encryption and data retention policies can protect archived organizational data.
- Securing data in use — some DLP systems can monitor and flag unauthorized activities that users may intentionally or unintentionally perform in their interactions with data.
- Data identification — it is crucial to determine if data needs to be protected or not. Data can be defined as sensitive either done manually by applying rules and metadata, or automatically via techniques like machine learning.
- Data leak detection — DLP solutions and other security systems like IDS, IPS, and SIEM, identify data transfers that are anomalous or suspicious. These solutions also alert security staff of a possible data leak.
DLP Solutions and File Security Solutions
File Security Solutions, such as Imperva File Firewall, are an important part of a DLP strategy. Such solutions safeguard data at rest and data in use, and detect leaks of file-based data.
Imperva File Firewall helps prevent data leaks by:
- Monitoring access to all sensitive files and recording granular usage data such as user, department, file accessed, file type and operation response time.
- Alerting on, and automatically blocking, file actions that violate security policies.
- Detecting abnormal or suspicious user behavior using machine learning, to detect insider threats.
- Mitigating Ransomware attacks by detecting and blocking typical file access patterns.
- Auditing and reporting on all file operations for compliance and investigation purposes.
Benefits of a DLP solution
DLP benefits begin with the ability to classify and monitor your data and include improving your overall visibility and control.
- Automate data classification Automated classification gathers information, such as when a document was created, where it’s stored, and how it’s shared, to improve the quality of data classification in your organization. A DLP solution uses this information to enforce your DLP policy, which helps prevent sensitive data from being shared with unauthorized users.
- Maintain regulatory compliance Every organization must adhere to data protection standards, laws, and regulations like HIPAA, the Sarbanes-Oxley (SOX) Act, and the Federal Information Security Management Act (FISMA). A DLP solution gives you the reporting capabilities you need to complete compliance audits, which may also include having a data-retention plan and training program for your employees.
DLP adoption and deployment
When adopting a data loss prevention solution, it’s important to do thorough research and find a vendor whose solution is appropriate for your needs.
To deploy your DLP solution with minimal downtime and avoid costly mistakes, your organization can: 1. Document the deployment process. Ensure your organization has procedures to follow, reference material for new team members, and records for compliance audits.
2. Define your security requirements. Help protect your organization’s intellectual property and your employees’ and customers’ personal information.
3. Establish roles and responsibilities. Clarify who’s accountable, who needs to be consulted, and who needs to be informed regarding activities related to your DLP solution. For example, your IT team must take part in the deployment so that they understand the changes being made and are able to resolve issues.
Data loss prevention tools and technologies

There are two types of DLP solutions on the market today: dedicated and integrated.
Dedicated products are standalone ones that are in-depth and complex. Integrated products are more basic; they work with other security tools to provide DLP policy enforcement and are less expensive than dedicated DLP tools.
DLP software products use business rules to enforce regulatory compliance and classify and protect confidential and critical information. This means unauthorized users can’t accidentally or maliciously share data that poses an organizational risk.
It’s doubtful one tool will meet all of an organization’s data loss prevention needs. Many DLP vendors have one area of focus, while others have suites of tools that fit together. Businesses can assemble a set of best-of-breed tools or use an all-in-one suite.
DLP Statistics
47% increase in data breaches since 2020
While malicious attackers are often the primary target of concern, it’s a popular misconception that they’re the leading cause of data loss. External breaches still account for over half of all data breaches. However, internal data breaches are also increasing and account for nearly half of all data breaches. Many data breaches are not from outsiders but from uninformed, negligent, or disgruntled employees.
84% of IT leaders say DLP is more difficult with a remote workforce
With more staff working from home, administrators are also challenged to protect data on personal devices and in the cloud. This makes DLP more problematic as a remote workforce adds risks compared to internal data on corporate-controlled devices.
60% to 70% of all data breaches warrant public disclosure
This statistic typically damages a company’s reputation. A study by Intel found that 70% of data loss cases in smaller organizations like SMEs or SMBs resulted in substantial financial damage or warranted public disclosure.
Challenges of DLP
Despite these benefits, there are also challenges with both implementing and maintaining DLP systems:
- Complexities. Configuration and management of many data sources can become complicated depending on how much data an organization is handling and how many employees are using the platform, each with their own levels of access.
- Employee training. These systems require employee training and regular messaging with updates. This is an extra expense and effort.
- False positives. False positives can occur with DLP platforms, as benign activities can be flagged as threats, causing alert fatigue as employees divert time and resources unnecessarily.
Applications of Data Loss Prevention (DLP)
Data Loss Prevention (DLP) is a critical cybersecurity measure designed to protect sensitive information from unauthorized access, use, or disclosure. Here are some key applications of DLP:
1. Protecting Sensitive Data:
- Personally Identifiable Information (PII): Safeguarding data like names, addresses, Social Security numbers, credit card details, and medical records.
- Intellectual Property: Protecting trade secrets, patents, copyrights, and other proprietary information.
- Financial Data: Securing bank account numbers, transaction records, and other financial information.
2. Compliance with Regulations:
- General Data Protection Regulation (GDPR): Ensuring compliance with European data privacy laws.
- Health Insurance Portability and Accountability Act (HIPAA): Protecting patient health information.
- Payment Card Industry Data Security Standard (PCI DSS): Protecting credit card data.
- Other industry-specific regulations: Adhering to data privacy requirements in various sectors.
3. Preventing Data Breaches:
- Insider Threats: Detecting and preventing unauthorized access or data exfiltration by employees.
- External Threats: Protecting against malicious attacks like phishing, malware, and ransomware.
- Accidental Data Loss: Preventing accidental deletion or leakage of sensitive data.
4. Enforcing Data Usage Policies:
- Restricting Data Access: Limiting access to sensitive data based on user roles and permissions.
- Monitoring Data Usage: Tracking how data is used and shared within the organization.
- Enforcing Data Retention Policies: Ensuring compliance with data retention and destruction requirements.
5. Improving Data Visibility and Control:
- Data Discovery: Identifying and classifying sensitive data across the organization.
- Data Mapping: Understanding the flow and storage of data.
- Data Governance: Establishing and enforcing policies for data management.
Common DLP Features:
- Data Classification: Identifying and categorizing data based on sensitivity levels.
- Content Monitoring: Analyzing data content for keywords, patterns, or indicators of unauthorized activity.
- Network Traffic Monitoring: Inspecting network traffic for suspicious data transfers.
- Endpoint Protection: Securing devices like laptops, smartphones, and tablets.
- Data Encryption: Protecting data at rest and in transit.
- Incident Response: Providing tools for detecting, investigating, and responding to data breaches.
DLP best practices
Follow these best practices to help ensure successful data loss prevention:
- Identify and classify sensitive data. To protect your data, you need to know what you’ve got. Use your DLP policy to identify sensitive data and label it accordingly.
- Use data encryption. Encrypt data that is at rest or in transit so unauthorized users won’t be able to view file content even if they gain access to its location.
- Secure your systems. A network is only as secure as its weakest entry point. Limit access to employees who need it to do their jobs.
- Implement DLP in phases. Know your business priorities and establish a pilot test. Allow your organization to grow into the solution and all it has to offer.
- Implement a patch management strategy. Test all patches for your infrastructure to ensure there are no vulnerabilities being introduced into your organization.
- Allocate roles. Establish roles and responsibilities to clarify who is accountable for data security.
- Automate. Manual DLP processes are limited in scope and can’t scale to meet the future needs of your organization.
- Use anomaly detection. Machine learning and behavioral analytics can be used to identify abnormal behavior that could result in a data leak.
- Educate stakeholders. A DLP policy isn’t enough to prevent intentional or accidental incidents; stakeholders and users must know their role in protecting your organization’s data.
- Establish metrics. Tracking metrics—like the number of incidents and time-to-response—will help determine the effectiveness of your DLP strategy.
Conclusion
In conclusion, DLP is an essential tool for organizations of all sizes that want to protect their sensitive data, maintain compliance, and mitigate the risks associated with data breaches. By investing in DLP solutions and implementing best practices, organizations can significantly improve their cybersecurity posture and safeguard their reputation. Data Loss Prevention (DLP) is a critical cybersecurity measure that plays a vital role in protecting sensitive information from unauthorized access, use, or disclosure.
FAQs
Data Loss Prevention (DLP) is a technology that helps organizations protect sensitive data from unauthorized access, use, or disclosure. It involves a combination of hardware, software, and policies to identify, monitor, and prevent data breaches.
DLP is essential for organizations because data breaches can have severe consequences, including financial losses, reputational damage, and legal liabilities. By implementing DLP measures, organizations can reduce the risk of data breaches and protect their sensitive information.
Implementing DLP can be challenging due to factors such as:
Complexity: DLP solutions can be complex to configure and manage.
Cost: Implementing and maintaining a DLP solution can be expensive.
False positives: DLP systems may sometimes flag legitimate activities as suspicious.
Resistance from employees: Some employees may resist DLP measures due to concerns about privacy or productivity.