Cybersecurity risk management is the process of identifying an organization’s digital assets, reviewing existing security measures, and implementing solutions to either continue what works or to mitigate security risks that may pose threats to a business. This type of ongoing vulnerability risk management (VRM) is crucial as the organization and the external threat landscape evolves.
VRM is an ongoing part of all business operations. New exploits are discovered, followed by patches released to fix them. New potentially vulnerable devices that increase the attack surface are frequently added to the network. This is especially true with the significant growth of Internet of Things (IoT) devices and sensors that are being placed in many physical locations.

Why is Cybersecurity Risk Management Important?
Cybersecurity risk management is important because it helps a business assess its current cybersecurity risk profile. This informs decisions the security organization will make moving forward in order to reduce the level of risk and address vulnerabilities.
Cybersecurity risk management is also important because it helps to bring about situational awareness within a security organization. Simply put, analysts don’t know what they don’t know. Awareness is the ability to look at all the information available, recognize what’s important, and act accordingly.
It’s essential to have a clear understanding of the risks in your organization and those that might arise in the future. You can assess awareness according to three distinct levels:
- Situational awareness: An organization understands the critical – people, data, and process – and operational elements for executing information-security strategy.
- Situational ignorance: Organizations assume everything is OK without considering the impact of people, data, and processes. They may be implementing security controls and awareness training, but there is no straightforward process or strategy that aligns to risk reduction and mitigation. In this scenario, budgets continue to creep ever upward.
- Situational arrogance: Organizations continue to spend big, while being routinely compromised and breached. In fact, they may actually take into account people, data, and process, but they fail to act because of other budgetary priorities. In this scenario, it may only be a matter of time before a business’ reputation is severely damaged due to continuous inability to defend against attacks.
- Cybersecurity risk management is the overarching umbrella under which specific kinds of security risk mitigations fall. Implementing a strategy to assess, identify, mitigate, and remediate vulnerability and risk is critical to every security organization operating on any level in any sector.
15 Tips for Developing Your Cyber Risk Management Strategy
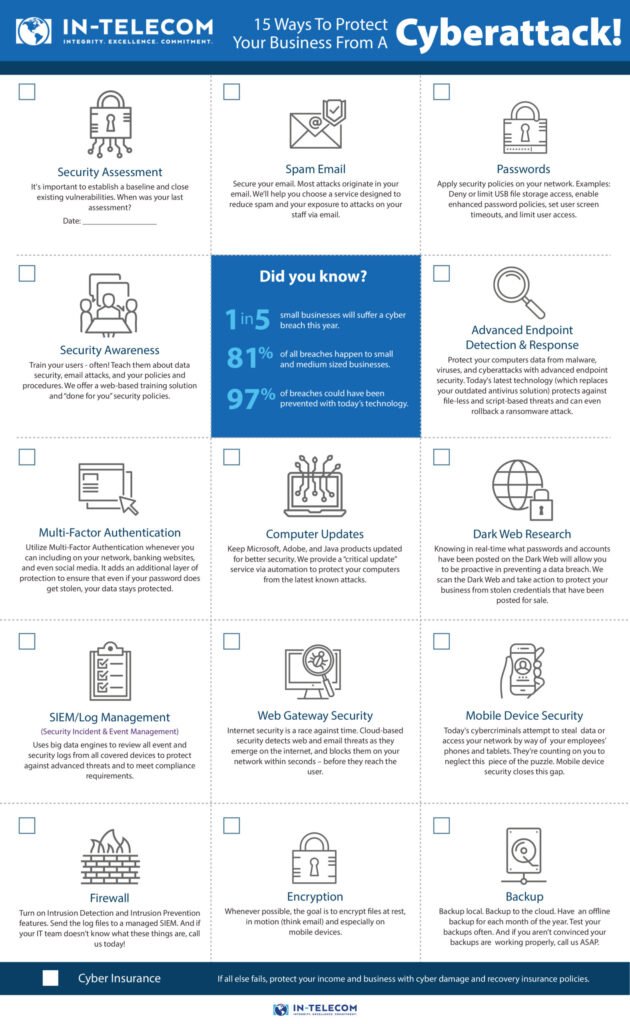
1. Build a Risk Management Culture
Leaders must establish a culture of cybersecurity and risk management initiatives throughout their organization. By defining a governance structure and communicating intent and expectations, leaders and managers can ensure appropriate employee involvement, accountability, and training.
With the average cost of a cyber attack exceeding $1.1 million, a risk management culture is a must. In addition to financial costs, there is a significant business impact – 54% of companies experience a loss in productivity, 43% have negative customer experiences, and 37% see a loss in brand reputation.
2. Ensure Proper Cyber Hygiene
Implementing good cyber hygiene practices is the starting point for cyber risk management.
The European Union’s Agency for Network and Information Security (ENISA) states that “cyber hygiene should be viewed in the same manner as personal hygiene and, once properly integrated into an organization, will be simple daily routines, good behaviors, and occasional checkups to make sure the organization’s online health is in optimum condition”.
3. Ensure You Comply With Relevant Regulations
Risk management, particularly Third-Party Risk Management and Vendor Risk Management, are increasingly part of regulatory compliance requirements.
This is especially true if you work in healthcare (HIPAA) or financial services (CPS 234, PCI DSS, 23 NYCRR 500). With that said, the introduction of general data protection laws like GDPR, LGPD, the SHIELD Act, PIPEDA, CCPA, and FIPA means most organizations have risk management requirements.
4. Distribute Responsibility
The burden for cybersecurity and enterprise risk management, in general, cannot solely rest with your IT security team.
While cybersecurity professionals do their best to ensure that all risks are accounted for, no security program can be successfully implemented without participation from the entire organization.
5. Pay Attention to Your Threat Environment
CISOs often don’t take into account the environment they are working in. Organizations should consider investing in OPSEC and social media training for their high-profile executives. Cybercriminals increasingly use information from public sources like LinkedIn or Facebook to launch sophisticated whaling attacks.
A whaling attack is a type of phishing attack that targets high-level executives, such as the CEO or CFO, to steal sensitive information from a company. This could include financial information or employees’ personal information.
6. Invest in Security Awareness Training
To implement your cybersecurity plan, you need fully trained staff at all levels who are capable of identifying risks and running the processes and procedures needed to mitigate those risks.
A good security awareness program should educate employees about corporate policies and procedures for working with IT assets and sensitive data. Employees should know who to contact if they think they’ve discovered a security threat and be taught which data should not be exposed over email.
Regular training is necessary for any organization, particularly those who rely heavily on third-party vendors or temporary staff.
7. Share Information
Security is a team sport. All stakeholders must be aware of risks, particularly those shared across departments.
Information about what cybersecurity risks your organization is worried about must be communicated to all appropriate stakeholders, especially those involved in decision-making. Everyone needs to be aware of the potential business impact of cyber attacks and how they can help prevent them.
Information-sharing tools, such as dashboards of relevant metrics, can keep stakeholders aware and involved.
8. Implement a Cybersecurity Framework
It’s important to implement an appropriate cybersecurity framework for your organization. This is typically dictated by the standards adopted by your industry or regulatory requirements. With this in mind, the most frequently adopted cybersecurity frameworks are:
- Payment Card Industry Data Security Standards (PCI DSS) — An information security standard for organizations that handle branded credit cards from major credit card schemes.
- ISO 27001 — ISO of the most well-known and well-used information security standards and is part of the ISO/IEC 27000 family of standards. It is published by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC).
- CIS Critical Security Controls — A prioritized set of actions for cybersecurity that form a defense-in-depth set of specific and actionable best practices to mitigate the most common cyber attacks. A principal benefit of CIS Controls is that they prioritize and focus on a small number of actions that greatly reduce cybersecurity risk.
- NIST Cybersecurity Framework (NIST CSF) — A framework based on existing standards, guidelines, and practices for private sector organizations in the United States to manage better and reduce cybersecurity risk.
9. Prioritize Cybersecurity Risk Remediation
Your organization has a limited budget and staff. To prioritize risks and responses, you need information, such as trends over time, potential impact, the likelihood of impact, and when the risk may materialize (near term, medium term, long term).
Simply put, you cannot protect against all possible threats. Organizations must review their risk profiles, identify which risks to remediate or mitigate first, and implement the necessary security measures to protect their most critical assets from threats.
10. Encourage Different Points of View
Too often, risks are viewed from a single viewpoint from a single source, such as the results of penetration testing, artificial intelligence, machine learning algorithms, personal experience, or company history.
The issue is that cyber criminals rarely share this same viewpoint. Malicious actors are more likely to think out of the box or use your external security posture to identify weak points in your system that you may not have considered.
For this reason, it’s important to encourage team members from all disciplines to think of and argue different attack scenarios. This sort of diverse thinking helps identify more risks and potential scenarios.
11. Emphasize Speed
A quick response can minimize the impact when your organization is exposed to a risk. Identifying high risks early can help your team start the remediation process before they are exploited.
For example, we detected data exposed in a GitHub repository by an AWS engineer in 30 minutes. We reported it to AWS, and the repo was secured the same day.
This repo contained personal identity documents and system credentials, including passwords, AWS key pairs, and private keys.
12. Develop a Repeatable Risk Assessment Process
A cybersecurity risk assessment is about understanding, managing, controlling, and mitigating cyber risk across your organization.
A repeatable process is crucial to any organization’s risk management strategy and data protection efforts.
To begin, you’ll need to audit your data to answer the following questions:
- What data do we collect?
- How and where are we storing this data?
- How do we protect and document the data?
- How long do we keep data?
- Who has access internally and externally to the data?
- Is the place we are storing the data properly secured?
You’ll then need to define the parameters of the risk assessment. Here are a few good questions to help you decide:
- What is the purpose of the assessment?
- What is the scope of the assessment?
- Are there any priorities or constraints I should be aware of that could affect the assessment?
- Who do I need access to in the organization to get all the information I need?
- What risk model does the organization use for risk analysis?
13. Implement an Incident Response Plan
An incident response plan is a set of written instructions that outline your organization’s response to data breaches, data leaks, cyber attacks, and security incidents.
Implementing an incident response plan is important because it outlines how to minimize the duration and impact of security incidents, identifies key stakeholders, streamlines digital forensics, improves recovery time, and reduces negative publicity and customer churn.
Even small cybersecurity incidents, like malware infections, when left unchecked, can snowball into bigger problems, leading to data breaches, data loss, and interrupted business operations.
14. Don’t Forget About Your Third and Fourth-Party Vendors
Remember that your cyber risk management responsibility doesn’t end with your internal information technology assets. You need to ensure your entire supply chain, which includes third-party vendors and their vendors (fourth parties), is invested in risk mitigation initiatives such as Vendor Risk Management and the implementation of a Third-Party Risk Management framework.
15. Use Technology to Reduce the Operational Overhead of Cyber Risk Management
Security ratings are a great way to instantly identify high-risk vendors and internal assets in real-time. They’re a data-driven, objective, and dynamic measure of an organization’s security posture. The key idea is the higher the security rating, the better the organization’s security posture.
Just as credit ratings and FICO scores aim to provide a quantitative measure of credit risk, security ratings aim to provide a quantitative measure of cyber risk. And just like credit ratings, they make it easy for even non-technical stakeholders to assess the security risk of a particular vendor or asset.
Certain software and technology, like Up Guard, can help any organization streamline its risk management processes and help reduce the amount of time, resources, and manpower required to reduce risks.
What is a Cybersecurity Risk Assessment?
A cybersecurity risk assessment is a process that helps organizations determine key business objectives and then identify the appropriate IT assets required to realize their objectives.
It involves the identification of cyber attacks that may negatively impact these IT assets. The organization is required to determine the likelihood of the occurrence of these attacks, and define the impact each attack may incur.
A cybersecurity risk assessment should map out the entire threat environment and how it can impact the organization’s business objectives.
The result of the assessment should assist security teams and relevant stakeholders in making informed decisions about the implementation of security measures that mitigate these risks.
What Are Cyber Threats?
The term cyber threat generally applies to any vector that can be exploited in order to breach security, cause damage to the organization, or exfiltrate data.
Common threat categories facing modern organizations include:
- Adversarial threats—including third-party vendors, insider threats, trusted insiders, established hacker collectives, privileged insiders, ad hoc groups, suppliers, corporate espionage, and nation-states.
- Human Error:
- Accidental deletion of data, incorrect configuration, unauthorized access.
- Insider Threats:
- Employees, contractors, or partners misusing access privileges.
- Data theft, sabotage, espionage.
- System Failures:
- Hardware or software malfunctions.
- Challenges in Cybersecurity Risk Management
- Evolving Threat Landscape: New threats emerge constantly.
- Complex IT Environments: Hybrid cloud, IoT, and mobile devices increase complexity.
- Shortage of Skilled Professionals: Difficulty finding qualified cybersecurity experts.
- Cost and Resource Constraints: Limited budgets and personnel.
- Regulatory Compliance: Meeting industry-specific regulations.
- Third-Party Risks: Managing security risks from external vendors.
- Risk Assessment: Identify and prioritize potential threats.
- Threat Intelligence: Stay informed about emerging threats.
- Employee Training: Educate staff about security best practices.
- Access Controls: Implement strong authentication and authorization.
- Network Security: Protect network infrastructure with firewalls, intrusion detection systems, etc.
- Data Protection: Encrypt sensitive data, implement data loss prevention measures.
- Incident Response Plan: Develop a plan for handling security breaches.
- Business Continuity Planning: Ensure operations can continue after a disruption.
- Regular Monitoring and Auditing: Continuously assess security posture.

Solutions for Cybersecurity Risk Management
Addressing the complexities of cybersecurity risk management requires a multi-faceted approach. Here are some key solutions:
Strategic Approaches
- Risk-Based Approach: Identify, assess, and prioritize risks based on their potential impact and likelihood. This allows for focused resource allocation.
- Strong Cybersecurity Governance: Establish clear roles, responsibilities, and accountability for cybersecurity within the organization.
- Continuous Risk Assessment: Regularly evaluate the threat landscape and organizational vulnerabilities to adapt security measures accordingly.
- Incident Response Plan: Develop a comprehensive plan to respond to and recover from cyberattacks.
- Employee Training and Awareness: Educate employees about cybersecurity best practices, social engineering tactics, and the importance of data protection.
Technological Solutions
- Network Security: Implement firewalls, intrusion detection and prevention systems (IDPS), and virtual private networks (VPNs).
- Endpoint Protection: Protect devices like laptops, desktops, and mobile devices with antivirus, anti-malware, and endpoint detection and response (EDR) solutions.
- Data Security: Employ encryption, data loss prevention (DLP), and access controls to safeguard sensitive information.
- Identity and Access Management (IAM): Implement strong authentication methods, authorization controls, and identity management systems.
- Security Information and Event Management (SIEM): Collect, analyze, and correlate security data to identify threats and anomalies.
- Threat Intelligence: Leverage threat intelligence feeds to stay informed about emerging threats and vulnerabilities.
- Cloud Security: Adopt robust cloud security measures, including access controls, data encryption, and vulnerability management.
Organizational Culture
- Security-Conscious Culture: Foster a culture where cybersecurity is a shared responsibility.
- Third-Party Risk Management: Implement processes to assess and manage risks associated with third-party vendors.
- Business Continuity and Disaster Recovery: Develop plans to ensure business continuity in case of a cyberattack.
Regulatory Compliance
- Stay Informed: Keep up-to-date with relevant cybersecurity regulations (e.g., GDPR, CCPA, HIPAA, PCI DSS).
- Risk Assessment: Conduct regular assessments to identify compliance gaps and develop remediation plans.
- Documentation: Maintain thorough documentation of compliance efforts.
Cyber Risk Management Frameworks
There are several cyber risk management frameworks, each of which provides standards organizations can use to identify and mitigate risks. Senior management and security leaders use these frameworks to assess and improve the security posture of the organization.
NIST CSF
The National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) is a popular framework. The NIST CSF framework provides a comprehensive set of best practices that standardize risk management. It defines a map of activities and outcomes related to the core functions of cybersecurity risk management—protect, detect, identify, respond, and recover.
ISO 27001
The International Organization for Standardization (ISO) has created the ISO/IEC 270001 in partnership with the International Electrotechnical Commission (IEC). The ISO/IEC 270001 cybersecurity framework offers a certifiable set of standards defined to systematically manage risks posed by information systems. Organizations can also use the ISO 31000 standard, which provides guidelines for enterprise risk management.
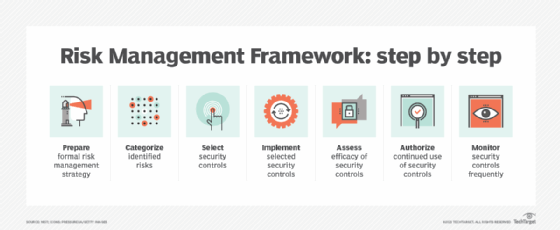
DoD RMF
The Department of Defense (DoD) Risk Management Framework (RMF) defines guidelines that DoD agencies use when assessing and managing cybersecurity risks. RMF splits the cyber risk management strategy into six key steps—categorize, select, implement, assess, authorize, and monitor.
FAIR Framework
The Factor Analysis of Information Risk (FAIR) framework is defined for the purpose of helping enterprises measure, analyze, and understand information risks. The goal is to guide enterprises through the process of making well-informed decisions when creating cybersecurity best practices.
Best Practices for Cybersecurity Risk Assessment
Build Cybersecurity into the Enterprise Risk Management Framework
Fully incorporate your risk-based cybersecurity program into the enterprise risk management framework, which functions as the organizing principle for analysing and classifying enterprise risks. The framework should not be used as a general guideline, but rather as the organizing principle. By framing cyber risk as a business risk, this approach makes cyber risk management more intelligible to businesses.
Identify Value-Creating Workflows
Identify the workflows that generate the greatest business value and define their associated risks. It is important to consider the potential impact of crucial workflows because these can also pose a significant risk. For example, payment processes create value but present a business risk, as they are vulnerable to fraud and data leakage.
Make sure the cybersecurity team knows which processes are regarded as valuable for your organization, and define the components (data assets, tools, teams) involved in each process. This allows you to apply the recommended controls. A collaborative approach involving both cybersecurity and business personnel is more effective than the one-sided maturity-based approach.
Prioritize Cyber Risks
Determine risk level based on the cost of prevention and value of information to inform your risk management and mitigation procedures. High-level risks should be addressed as soon as possible, while low-level risks can be addressed down the line or accepted as a tolerated risks. If the cost of protecting an asset is higher than its value, the expense is not worthwhile unless the risk may impact your reputation.
Implement Ongoing Risk Assessments
Perform continuous, adaptive, and actionable risk identification and assessment to keep up with evolving cybersecurity threats and solutions. Regularly review risk management processes to identify and remediate gaps. Cybersecurity teams rely on actionable insights from risk assessments to secure digital environments and assets.
Continuous Monitoring and Review
- Regular assessments: Conduct ongoing risk assessments to stay updated on the threat landscape.
- Risk register: Maintain a risk register to track identified risks, mitigation strategies, and residual risks.
Risk Mitigation
- Develop response plans: Create strategies to mitigate identified risks.
- Implement controls: Employ technical, administrative, and physical controls to reduce risks.
Challenges of Cybersecurity Risk Management

Cybersecurity risk management is a complex and ever-evolving field. Organizations face numerous challenges in effectively protecting their digital assets. Here are some of the most significant:
1. Evolving Threat Landscape
- New threats emerge constantly: Hackers are continually developing new attack vectors, making it difficult to stay ahead.
- Sophistication of attacks: Cyberattacks are becoming increasingly complex and targeted, requiring advanced defense mechanisms.
2. Resource Constraints
- Budget limitations: Allocating sufficient funds for cybersecurity can be challenging, especially for smaller organizations.
- Talent shortage: Finding qualified cybersecurity professionals is competitive and costly.
3. Complex IT Environments
- Hybrid and multi-cloud infrastructures: Managing security across diverse IT environments is complex.
- Internet of Things (IoT): The proliferation of IoT devices increases the attack surface.
4. Third-Party Risk
- Supply chain attacks: Vulnerabilities in third-party systems can compromise an organization’s security.
- Assessing vendor risk: Evaluating the security posture of third-party providers can be time-consuming and challenging.
5. Regulatory Compliance
- Complex regulations: Adhering to various cybersecurity regulations is burdensome.
- Evolving standards: Keeping up with changing regulatory requirements is difficult.
6. Human Error
- Employee mistakes: Accidental data breaches and security incidents can occur due to human error.
- Social engineering attacks: Phishing and other social engineering tactics remain effective.
7. Risk Quantification and Prioritization
- Measuring cyber risk: Determining the actual financial impact of cyberattacks is challenging.
- Prioritizing investments: Allocating resources effectively based on risk assessment can be difficult.
8. Lack of Awareness and Training
- Employee education: Many employees lack cybersecurity awareness and training.
- Culture of security: Fostering a security-conscious culture within the organization is essential but challenging.
9. Data Privacy Concerns
- Protecting sensitive data: Safeguarding personal and confidential information is critical.
- Compliance with privacy regulations: Adhering to data privacy laws like GDPR and CCPA is complex.
10. Decision Fatigue
- Overwhelming information: The volume of security alerts and data can lead to decision fatigue.
- Automation: Implementing automation to streamline decision-making is crucial.
Conclusion
Cybersecurity risk management is an indispensable component of modern organizational resilience. It’s a dynamic process that requires constant vigilance and adaptation to counter the ever-evolving threat landscape.
While challenges abound, including resource constraints, human error, and the complexities of modern IT environments, a comprehensive strategy can significantly mitigate risks. By combining strategic planning, technological advancements, and a strong organizational culture, organizations can effectively protect their assets and maintain business continuity.
Ultimately, cybersecurity risk management is not a destination but a journey. Organizations must commit to ongoing improvement and investment to safeguard their digital assets and build trust with stakeholders.
FAQs
Cybersecurity risk management is the systematic process of identifying, assessing, prioritizing, and addressing potential threats to an organization’s information systems. It involves protecting sensitive data, maintaining system integrity, and ensuring business continuity.
You can identify risks through vulnerability assessments, threat modeling, and risk assessments. Consider factors like your industry, the type of data you handle, and your IT infrastructure.
Common threats include phishing, malware, ransomware, DDoS attacks, and insider threats.
