Application security is the process of developing, adding, and testing security features within applications to prevent security vulnerabilities against threats such as unauthorized access and modification.
Application security may include hardware, software, and procedures that identify or minimize security vulnerabilities. A router that prevents anyone from viewing a computer’s IP address from the Internet is a form of hardware application security.

Tools used for Application security
- Dynamic application security testing: This automated application security test is best for internal-facing, low-risk applications that must comply with regulatory security assessments. For medium-risk applications and critical applications undergoing minor changes, using DAST with manual web security testing is the best solution to find common vulnerabilities.
- Static application security testing: This type of testing can be performed though automated and manual testing techniques. It identifies bugs without the need to execute applications in a production environment. It also enables developers to scan source code and systematically find and eliminate software security vulnerabilities.
- Pen testing: This manual application security test is best for critical applications, especially those undergoing major changes. The assessment involves business logic and adversary-based testing to discover advanced attack scenarios.
- Software composition analysis : This type of analysis helps teams manage the security, quality, and license compliance risks that come from the use of open source and third-party code in applications and containers.
How does application security work?
Security measures include improving security practices in the software development lifecycle and throughout the application lifecycle. All app activities should minimize the likelihood that malicious actors can gain unauthorized access to systems, applications or data. The ultimate goal of application security is to prevent attackers from accessing, modifying or deleting sensitive or proprietary data.
An application firewall is a countermeasure commonly used for software. Firewalls determine how files are executed and how data is handled based on the specific installed program. Routers are the most common countermeasure for hardware. They prevent the Internet Protocol (IP) address of an individual computer from being directly visible on the internet.
Why is application security important?
Application security — including the monitoring and managing of application vulnerabilities — is important for several reasons, including the following:
- Finding and fixing vulnerabilities reduces security risks and doing so helps reduce an organization’s overall attack surface.
- Software vulnerabilities are common. While not all of them are serious, even noncritical vulnerabilities can be combined for use in attack chains. Reducing the number of security vulnerabilities and weaknesses helps reduce the overall impact of attacks.
- Taking a proactive approach to application security is better than reactive security measures. Being proactive enables defenders to identify and neutralize attacks earlier, sometimes before any damage is done.
- As enterprises move more of their data, code and operations into the cloud, attacks against those assets can increase. Application security measures can help reduce the impact of such attacks.
Neglecting application security can expose an organization to potentially existential threats.
What is threat modeling?
Threat modeling or threat assessment is the process of reviewing the threats to an enterprise or information system and then formally evaluating the degree and nature of the threats. Threat modeling is one of the first steps in application security and usually includes the following five steps:
- rigorously defining enterprise assets;
- identifying what each application does or will do with respect to these assets;
- creating a security profile for each application;
- identifying and prioritizing potential threats; and
- documenting adverse events and the actions taken in each case.
In this context, a threat is any potential or actual adverse event that can compromise the assets of an enterprise. These include both malicious events, such as a denial-of-service attack, and unplanned events, such as the failure of a storage device.
Common application security weaknesses and threats
The most common application security weaknesses are well-known. Various organizations track them over time. The Open Web Application Security Project (OWASP) Top Ten list and the Common Weakness Enumeration (CWE) compiled by the information security community are two of the best-known lists of application weaknesses.
The OWASP list focuses on web application software. The CWE list focuses on specific issues that can occur in any software context. Its goal is to provide developers with usable guidance on how to secure their code.
The top 10 items on the CWE list and their CWE scores are the following:
| CWE | Description | CWE score |
| Out-of-bounds write | Software that improperly writes past a memory boundary can cause data corruption, system crash or enable malicious code execution. | 65.93 |
| Cross-site scripting | Improper neutralization of potentially harmful input during webpage automation enables attackers to hijack website users’ connections. | 46.84 |
| Out-of-bounds read | Software that improperly reads past a memory boundary can cause a crash or expose sensitive system information that attackers can use in other exploits. | 24.9 |
| Input validation attack | Lack of validation or improper validation of input or data enables attackers to run malicious code on the system. | 20.47 |
| Operating system (OS) command injection | Improper neutralization of potentially harmful elements used in an OS command. | 19.55 |
| SQL injection | Software that doesn’t properly neutralize potentially harmful elements of a SQL command. These flaws enable attacks against databases. | 19.54 |
| Use after free | Software that references memory that had been freed can cause the program to crash or enable code execution. | 16.83 |
| Path traversal | Improper limitation of a pathname to a restricted directory. | 14.69 |
| cross-site request forgery | When a web app fails to validate that a user request was intentionally sent, it may expose data to attackers or enable remote malicious code execution. | 14.46 |
| Unrestricted upload of malware or other potentially dangerous files | Software that permits unrestricted file uploads opens the door for attackers to deliver malicious code for remote execution. | 8.45 |
Best Practices for Application Security
Implementing and adhering to application security best practices helps create a strong foundation for effective security controls. It is important to integrate security considerations throughout the entire software development lifecycle and continuously reassess and improve security measures as new threats and vulnerabilities emerge.
- Shifting security left by incorporating security considerations early in the software development lifecycle. Integrate security practices, such as secure coding, threat modeling, and security testing, from the initial design phase to ensure potential vulnerabilities are addressed proactively.
- Implementing robust authentication mechanisms, such as strong passwords, multi-factor authentication (MFA), or biometric authentication to verify user identities. Enforce proper authorization controls to ensure users have appropriate access privileges, limiting access to sensitive resources and functionality, and preventing lateral spread and privilege escalation.
- Developing a risk-based approach to prioritize remediation efforts. Focus on addressing high-risk vulnerabilities first, based on their potential impact and exploitability. Establish a clear process for timely remediation.
- Implementing robust monitoring and logging mechanisms to detect and respond to security incidents effectively. Monitor for suspicious activities, failed login attempts, and anomalous behavior. Maintain audit logs to aid in incident investigation and response.
Ensuring Application Security
Application security is an ongoing process and requires a multi-layered approach to ensure comprehensive protections. Use the following check list to regularly reassess and update security practices to help ensure that your applications remain resilient against evolving security risks.
- Conduct thorough security assessments and code reviews. Perform comprehensive security assessments to identify potential vulnerabilities and weaknesses in your applications. This includes using automated tools to scan for common vulnerabilities and leveraging dynamic code analysis to uncover security flaws.
- Implement secure coding practices and frameworks. Adopt secure coding practices from the outset, including the use of industry-recognized coding standards and secure coding frameworks and libraries that have undergone rigorous security testing and are actively maintained by the developer community.
- Regularly update and patch applications. Secure third-party components and regularly update and patch libraries, frameworks, and dependencies used within the application to mitigate against known vulnerabilities.
- Perform vulnerability and penetration testing. Conduct regular vulnerability testing using automated scanning tools to identify potential vulnerabilities in the application, including Dynamic Application Security Testing (DAST). Perform penetration testing that simulates real-world attacks to evaluate the security posture of the application and uncover any weaknesses that automated tools may have missed. These findings can be incorporated into web application firewall security policies to provide a critical stopgap against vulnerability exploitation.
- Educate developers and promote a security-first mindset. Provide security training and awareness programs for developers to enhance their understanding of common vulnerabilities and secure coding practices. Emphasize the importance of implementing security throughout the development process and encourage .
Application Security Testing tools
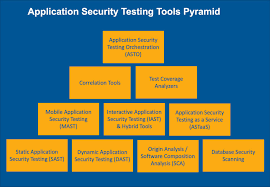
Application security testing plays a vital role in detecting and identifying vulnerabilities, weaknesses, and flaws before they can be exploited by attackers.
Penetration testing involves actively assessing an application’s security by simulating real-world attacks. In this test, skilled security professionals attempt to exploit vulnerabilities in the application to determine its resilience against different attack vectors.
Organizations often use a combination of these testing methods to achieve a thorough assessment of application security. Threat modeling tools such as STRIDE and DREAD can also provide useful guidance for employing these risk management techniques.
The Importance of Secure Coding and Vulnerability Management
Secure coding forms the foundation for building resilient and secure software applications. It involves following established coding standards, best practices, and guidelines to minimize the risk of introducing security flaws and common vulnerabilities, such as injection attacks, buffer overflows, or insecure direct object references, during the development process. Developers should stay up to date with the latest security countermeasures and defend against emerging threats by reducing the attack surface of the application
Exploring Application Security Controls
Application security controls are vital for safeguarding applications and protecting sensitive data. These include authentication controls, which ensure that users or systems attempting to access an application are verified and authorized. Strong authentication mechanisms, such as passwords, multi-factor authentication (MFA), or biometric authentication, validate user identities and protect against unauthorized access.
Application Security in the Cloud
As organizations harness the power of multiple cloud providers and leverage edge computing resources, the increasingly distributed nature of application design makes app security a much more complex endeavor.
Distributed cloud environments are often composed of modern, microservices-based applications that are designed to be modular, scalable, and interconnected. This architecture offers numerous benefits but also introduces new security risks. Each microservice represents a potential attack surface and avenue for lateral spread, necessitating specialized security measures.
Types of Application Security
Application security encompasses a wide range of practices and technologies designed to protect software applications from vulnerabilities and attacks. Here are some key types:
Fundamental Security Controls
- Authentication: Verifying a user’s identity to grant access.
- Authorization: Determining what actions a user can perform based on their identity and roles.
- Encryption: Converting data into a code to prevent unauthorized access.
- Input Validation: Ensuring data entered into an application is in the expected format and range.
- Error Handling: Managing unexpected errors gracefully to prevent information leakage.
- Logging and Monitoring: Recording application activity for auditing and troubleshooting.
Application Security Testing
- Static Application Security Testing (SAST): Analyzing application code without executing it to find vulnerabilities.
- Dynamic Application Security Testing (DAST): Testing running applications to identify vulnerabilities through simulated attacks.
- Interactive Application Security Testing (IAST): Combining SAST and DAST for more comprehensive testing.
- Runtime Application Self-Protection (RASP): Protecting applications in production by detecting and blocking attacks at runtime.
- Penetration Testing: Simulating real-world attacks to identify vulnerabilities.
Additional Security Measures
- Web Application Firewall (WAF): Filtering and monitoring incoming web traffic to protect against attacks.
- Security Code Reviews: Manually inspecting code for vulnerabilities.
- Secure Coding Practices: Following guidelines to write secure code from the beginning.
- Incident Response Plan: Having a plan in place to respond to security incidents.
- Security Awareness Training: Educating employees about security best practices.
Specific Application Security Areas
- API Security: Protecting Application Programming Interfaces (APIs) from unauthorized access.
- Mobile Application Security: Securing mobile apps from vulnerabilities and data breaches.
- Cloud Application Security: Protecting applications deployed in cloud environments.
Challenges in Application Security
Application security is a complex and ever-evolving field. Organizations face numerous challenges in securing their applications. Here are some of the most common:
Development-Related Challenges
- Lack of Security Awareness: Many developers prioritize functionality over security.
- Time-to-Market Pressure: Rapid development cycles often lead to security shortcuts.
- Complex Codebases: Large, legacy applications can be difficult to secure.
- Third-party Components: Relying on external libraries introduces potential vulnerabilities.
- Insecure Coding Practices: Developers may not be aware of secure coding guidelines.
Security Testing Challenges
- Tool Limitations: Security testing tools often have false positives and negatives.
- Testing Coverage: It’s difficult to test all possible attack vectors.
- Cost and Time: Comprehensive security testing can be expensive and time-consuming.
Organizational Challenges
- Prioritization: Security often takes a backseat to other business priorities.
- Budget Constraints: Limited resources can hinder security investments.
- Skill Shortages: Finding qualified security professionals can be challenging.
- Regulatory Compliance: Adhering to security regulations can be complex.
- Changing Threat Landscape: The evolving nature of threats requires constant adaptation.
Technical Challenges
- Vulnerability Management: Identifying, prioritizing, and patching vulnerabilities is time-consuming.
- Data Protection: Safeguarding sensitive data from breaches is a constant challenge.
- Cloud Security: Ensuring security in dynamic cloud environments is complex.
- Mobile Application Security: Protecting mobile apps from various threats is challenging.
- API Security: Securing APIs from attacks is crucial but often overlooked.
Addressing these challenges requires a comprehensive approach that involves collaboration between development, security, and business teams. It’s essential to integrate security into the entire software development lifecycle (SDLC) and continuously invest in security measures, training, and tools.
Risks of Application Security Failures
The consequences of inadequate application security can be catastrophic for organizations. Here are some of the primary risks:
Financial Loss
- Direct costs: Incident response, legal fees, public relations, and remediation expenses.
- Loss of revenue: Disruption of services, customer churn, and damage to brand reputation.
- Regulatory fines: Non-compliance with data protection regulations.
Reputation Damage
- Loss of trust: Customers, partners, and investors may lose confidence in the organization.
- Negative publicity: Security breaches can lead to negative media coverage.
- Brand erosion: Damage to the organization’s image and reputation.
Data Loss and Breach
- Exposure of sensitive information: Customer data, financial information, intellectual property, and trade secrets can be compromised.
- Identity theft: Personal information of customers and employees can be stolen.
- Data extortion: Threat actors may demand ransom for stolen data.
Legal and Regulatory Issues
- Non-compliance with regulations: Organizations may face penalties for violating data protection laws.
- Lawsuits: Customers and partners may sue for damages.
- Criminal charges: In severe cases, individuals responsible for the breach may face criminal charges.
Business Disruption
- System downtime: Security incidents can disrupt critical business operations.
- Supply chain disruptions: Attacks on third-party systems can impact the organization.
- Loss of productivity: Employees may be unable to work due to security incidents.
Competitive Advantage Loss
- Loss of market share: Competitors may gain an advantage if the organization’s reputation is damaged.
- Intellectual property theft: Competitors may gain access to valuable information.
To mitigate these risks, organizations must prioritize application security and implement robust measures to protect their applications and data.
Solutions for Application Security
Addressing application security requires a multi-faceted approach that involves people, processes, and technology. Here are some key solutions:
People centric solution
- Security Awareness Training: Educate employees about security best practices, social engineering tactics, and the importance of protecting sensitive data.
- DevSecOps Culture: Foster a culture where security is integrated into the development lifecycle from the outset.
- Security Champions: Identify and empower individuals who can drive security initiatives within the organization.
Process-Centric Solutions
- Secure Software Development Lifecycle (SDLC): Incorporate security into every phase of development, from design to deployment.
- Threat Modeling: Identify potential threats and vulnerabilities early in the development process.
- Incident Response Plan: Develop a comprehensive plan for responding to security incidents.
- Regular Security Assessments: Conduct vulnerability assessments and penetration testing to identify weaknesses.
Technology-Centric Solutions
- Web Application Firewalls (WAFs): Protect web applications from common attacks.
- Intrusion Detection and Prevention Systems (IDPS): Monitor network traffic for malicious activity.
- Security Information and Event Management (SIEM): Collect, analyze, and correlate security data.
- Encryption: Protect sensitive data both at rest and in transit.
- Access Controls: Implement strong authentication and authorization mechanisms.
- Security Testing Tools: Utilize static and dynamic application security testing (SAST and DAST) to identify vulnerabilities.
- Container and Cloud Security: Protect applications running in containerized or cloud environments.
Additional Considerations
- Patch Management: Keep software and systems up-to-date with the latest patches.
- Third-Party Risk Management: Assess the security posture of third-party vendors.
- Data Loss Prevention (DLP): Prevent sensitive data from being exfiltrated.
- Business Continuity and Disaster Recovery (BCDR): Ensure business continuity in case of a security incident.
By combining these elements and tailoring them to specific organizational needs, it’s possible to significantly enhance application security and reduce the risk of breaches.
Benefits of application security
Businesses rely on applications to power nearly everything they do, so keeping them secure is nonnegotiable. Below are some of the many benefits of investing in application security:
- Reduced risk from both internal and third-party sources – By eliminating as many vulnerabilities as possible, you can increase your potential to ward off attacks.
- Increased confidence and trust from customers – By demonstrating that your applications are secure and trustworthy, you help increase customer confidence, which could also breed loyalty and positive word of mouth.
- Maintenance of brand image – Attacks put businesses in the headlines, and that is unwanted publicity.
- Increased trust from third-party stakeholders, clients, and partners – People want to do business with companies they trust.
- Reduced disruption to operations – By identifying potential security issues and resolving them before they lead to a full-on attack or loss of data, you can head off unwanted disruption to operations.
- Identification of issues during development phase – With the right AppSec solution, you can identify common attack vectors and risks during development and create a resolution strategy for them before releasing an application into production.
- Earlier awareness of potential risks – Most application security solutions are designed to identify security vulnerabilities and alert administrators to the existence of potential issues—so you can address the risks and eliminate vulnerabilities before an attacker can take advantage of them.
- Increased compliance with security mandates – Today’s data is subject to a wide variety of industry and government
Conclusion
Application security is an indispensable facet of modern cybersecurity. As the digital landscape evolves, so do the threats targeting applications. It’s no longer a standalone initiative but an integral component of overall organizational risk management.
To effectively safeguard applications, a holistic approach is essential. This involves a combination of human expertise, robust processes, and advanced technologies. By prioritizing security from the outset of development and maintaining a vigilant stance against emerging threats, organizations can significantly reduce their exposure to vulnerabilities.
Ultimately, application security is an investment in protecting an organization’s reputation, assets, and customers. By establishing a strong security culture and implementing comprehensive measures, businesses can build resilience against cyberattacks and thrive in the digital age.
FAQs
Application security is the process of protecting software applications from attacks by securing the data and code within the application.
It involves security measures implemented during application development, design, and deployment.
Application security is crucial to protect sensitive data, maintain customer trust, prevent financial loss, and comply with regulations.
A data breach can lead to significant reputational damage and legal consequences.
