Identity and Access Management (IAM) is a framework of policies, processes, and technologies that enable organizations to manage digital identities and control user access to critical corporate information. By assigning users with specific roles and ensuring they have the right level of access to corporate resources and networks, IAM improves security and user experience, enables better business outcomes, and increases the viability of mobile and remote working and cloud adoption.
Compromised user credentials are among the most common targets for hackers to gain entry into organizations’ networks through malware, phishing, and ransomware attacks. It is therefore vital for enterprises to safeguard their most valuable resources. Many are increasingly turning to Identity and Access Management (IAM) technology to protect their data and people.

The importance of IAM for organizations
One reason IAM is an important part of cybersecurity is that it helps an organization’s IT department strike the right balance between keeping important data and resources inaccessible to most but still accessible to some. IAM makes it possible to set controls that grant secure access to employees and devices while making it difficult or impossible for outsiders to get through.
Another reason that IAM is important is that cybercriminals are evolving their methods daily. Sophisticated attacks like phishing emails are one of the most common sources of hacking and data breaches and they target users with existing access. Without IAM, it’s difficult to manage who and what has access to an organization’s systems. Breaches and attacks can run rampant because not only is it difficult to see who has access, it’s also difficult to revoke access from a compromised user.
While perfect protection unfortunately doesn’t exist, IAM solutions are an excellent way to prevent and minimize the impact of attacks. Instead of restricting everyone’s access in the event of a breach, many IAM systems are AI-enabled and capable of detecting and stopping attacks before they become bigger problems.
How Identity and Access Management (IAM) Boosts Security
The core objective of an IAM platform is to assign one digital identity to each individual or a device. From there, the solution maintains, modifies, and monitors access levels and privileges through each user’s access life cycle.
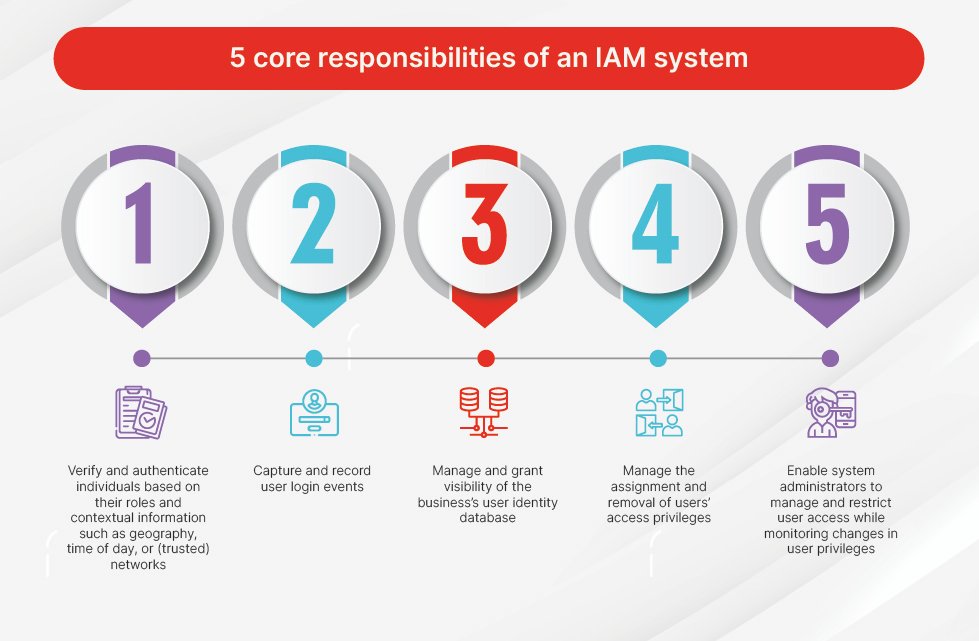
The core responsibilities of an IAM system are to:
- Verify and authenticate individuals based on their roles and contextual information such as geography, time of day, or (trusted) networks
- Capture and record user login events
- Manage and grant visibility of the business’s user identity database
- Manage the assignment and removal of users’ access privileges
- Enable system administrators to manage and restrict user access while monitoring changes in user privileges.
Role-Based Access Control
IAM frameworks are not only crucial to controlling user access to critical information but also implementing role-based access control. This enables system administrators to regulate access to corporate networks or systems based on individual users’ roles, which are defined by their job title, level of authority, and responsibility within the business.
Automatic De-Provisioning
An Identity and Access Management solution is also crucial to preventing security risks when employees depart a business. Manually de-provisioning access privileges to the apps and services the former employee used can often take time or even be forgotten entirely, leaving a security gap for hackers. IAM prevents this by automatically de-provisioning access rights once a user leaves the company or as their role within the organization changes.
Human and Device Identification
Digital identities do not just exist for humans, as IAM also manages the identity of devices and applications. This establishes further trust and provides deeper context around whether a user is who they say they are and the applications that users are entitled to access.
What is Identity and Access Management Composed Of?
An IAM solution consists of various components and systems. The most commonly deployed include:
1. Single Sign-On
Single sign-on (SSO) is a form of access control that enables users to authenticate with multiple software applications or systems using just one login and one set of credentials. The application or site that the user attempts to access relies on a trusted third party to verify that the user is who they say they are, resulting in:
- Enhanced user experience
- Reduced password fatigue
- Simplified password management
- Minimized security risks for customers, partners, and vendors
- Limited credential usage
- Improved identity protection
2. Multi-Factor Authentication
Multi-factor authentication verifies a user’s identity with requirements to enter multiple credentials and provide various factors:
- Something the user knows: a password
- Something the user has: a token or code sent to the user via email or SMS, to a hardware token generator, or to an authenticator application installed on the user’s smartphone
- Something specific to the user, such as biometric information
3. Privileged Access Management
Privileged access management protects businesses from both cyber and insider attacks by assigning higher permission levels to accounts with access to critical corporate resources and administrator-level controls. These accounts are typically high-value targets for cybercriminals and, as such, high risk for organizations.
4. Risk-Based Authentication
When a user attempts to log in to an application, a risk-based authentication solution looks at contextual features such as their current device, IP address, location, or network to assess the risk level.
Based on this, it will decide whether to allow the user access to the application, prompt them to submit an additional authentication factor, or deny them access. This helps businesses immediately identify potential security risks, gain deeper insight into user context, and increase security with additional authentication factors.
5. Data Governance
Data governance is the process that enables businesses to manage the availability, integrity, security, and usability of their data. This includes the use of data policies and standards around data usage to ensure that data is consistent, trustworthy, and does not get misused. Data governance is important within an IAM solution as artificial intelligence and machine learning tools rely on businesses having quality data.
7. Zero-Trust
A Zero-Trust approach moves businesses away from the traditional idea of trusting everyone or everything that is connected to a network or behind a firewall. This view is no longer acceptable, given the adoption of the cloud and mobile devices extending the workplace beyond the four walls of the office and enabling people to work from anywhere. IAM is crucial in this approach, as it allows businesses to constantly assess and verify the people accessing their resources.
IAM basic concepts
To understand IAM, you must be familiar with some fundamental concepts:
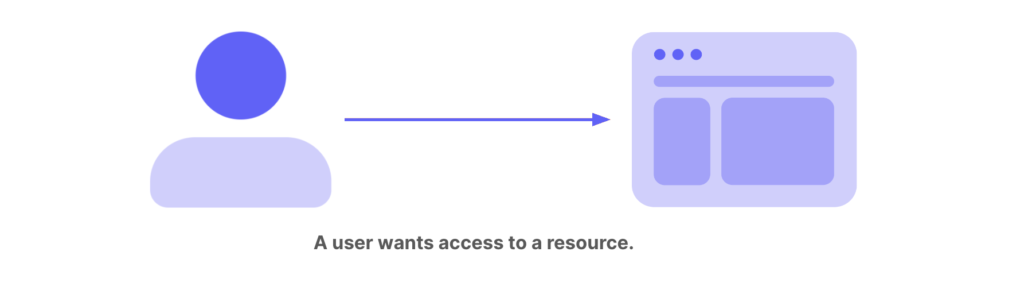
- A digital resource is any combination of applications and data in a computer system. Examples of digital resources include web applications, APIs, platforms, devices, or databases.
- The core of IAM is identity. Someone wants access to your resource. It could be a customer, employee, member, participant, and so on. In IAM, a user account is a digital identity. User accounts can also represent non-humans, such as software, Internet of Things devices, or robotics.
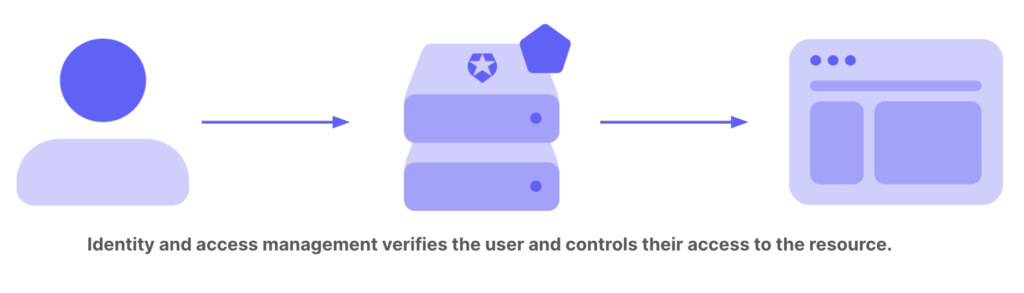
- Authentication is the verification of a digital identity. Someone (or something) authenticates to prove that they’re the user they claim to be.
- Authorization is the process of determining what resources a user can access.
The difference between authentication and authorization
It’s common to confuse authentication and authorization because they seem like a single experience to users. They are two separate processes: authentication proves a user’s identity, while authorization grants or denies the user’s access to certain resources.
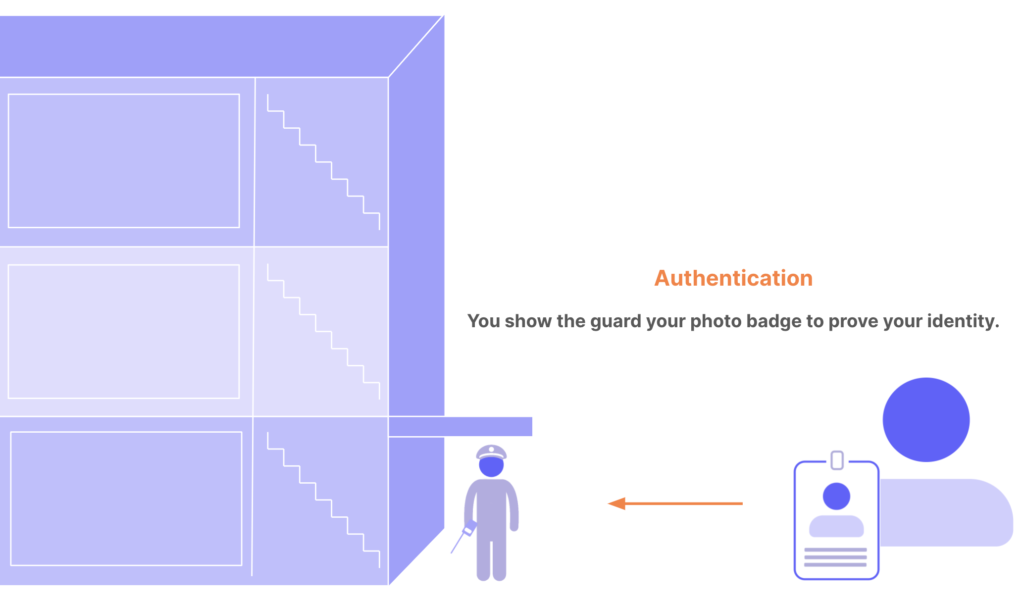
You can think of authentication and authorization as the security system for an office building. Users are the people who want to enter the building. Resources that people want to access are areas in the building: floors, rooms, and so on.
Authentication: When you enter the building, you must show your photo ID badge to the security guard. The guard compares the photo on the badge to your face. If they match, the guard lets you through the door to try to access different areas of the building. The guard doesn’t tell you what rooms you can access; they only get proof that you are who you claim to be. This is authentication: confirming user identity.
Authorization: In this scenario, imagine the elevators and doorways in the building have key sensors for access. The chip in your badge gives you access only to the first floor, which your company occupies. If you swipe your badge to enter any other floor, your access is denied. You can access your private office but not those belonging to your colleagues. You can enter the supply room but not the server room. This is authorization: granting and denying access to different resources based on identity.
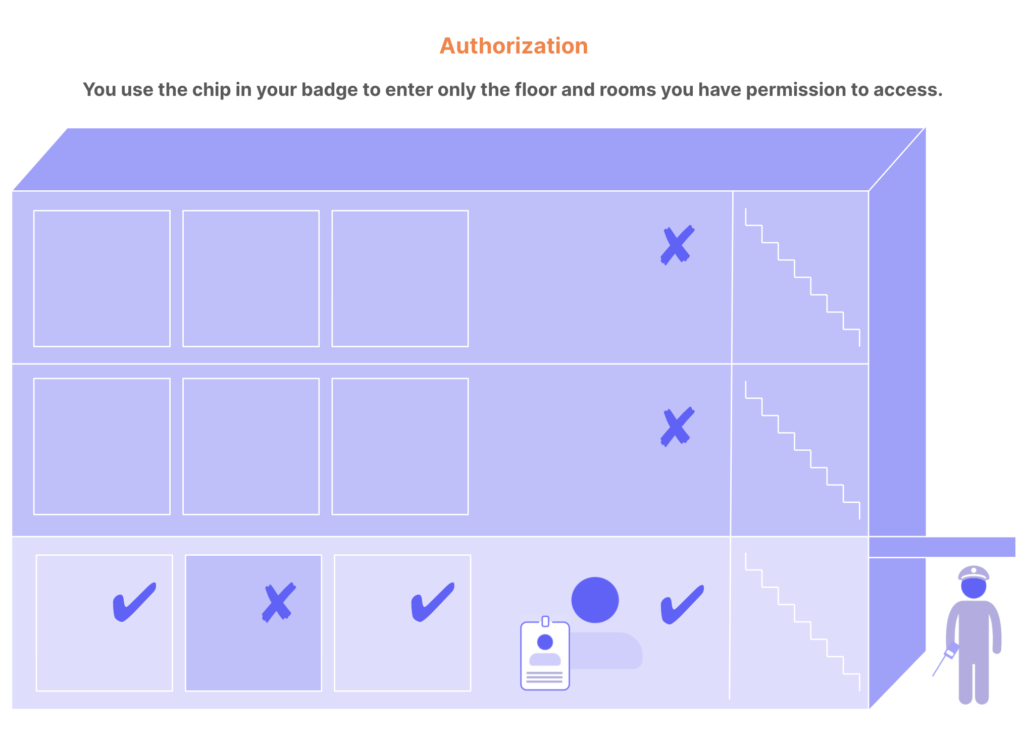
What does IAM do?
Identity and access management gives you control over user validation and resource access:
- How users become a part of your system
- What user information to store
- How users can prove their identity
- When and how often users must prove their identity
- The experience of proving identity
- Who can and cannot access different resources
You integrate IAM with your application, API, device, data store, or other technology. This integration can be very simple. For example, your web application might rely entirely on Facebook for authentication, and have an all-or-nothing authorization policy. Your app performs a simple check: if a user isn’t currently logged in to Facebook in the current browser, you direct them to do so. Once authenticated, all users can access everything in your app.
It’s unlikely that such a simple IAM solution would meet the needs of your users, organization, industry, or compliance standards. In real life, IAM is complex. Most systems require some combination of these capabilities:
- Seamless signup and login experiences: Smooth and professional login and signup experiences occur within your app, with your brand’s look and language.
- Multiple sources of user identities: Users expect to be able to log in using a variety of social (such as Google or Linked in), enterprise (such as Microsoft Active Directory), and other identity providers.
- Multi-factor authentication (MFA): In an age when passwords are often stolen, requiring additional proof of identity is the new standard. Fingerprint authentication and one-time passwords are examples of common authentication methods. To learn more, read Multi-Factor Authentication (MFA).
- Step-up authentication: Access to advanced capabilities and sensitive information require stronger proof of identity than everyday tasks and data. Step-up authentication requires additional identity verification for selected areas and features. To learn more, read Add Step-up Authentication.
- Attack protection: Preventing bots and bad actors from breaking into your system is fundamental to cybersecurity. To learn more, read Attack Protection.
How does IAM work?
“Identity and access management” is not one clearly defined system. IAM is a discipline and a type of framework for solving the challenge of secure access to digital resources. There’s no limit to the different approaches for implementing an IAM system. This section explores elements and practices in common implementations.
Identity providers
In the past, the standard for identity and access management was for a system to create and manage its own identity information for its users. Each time a user wanted to use a new web application, they filled in a form to create an account. The application stored all of their information, including login credentials, and performed its own authentication whenever a user signed in.
As the internet grew and more and more applications became available, most people amassed countless user accounts, each with its own account name and password to remember. There are many applications that continue to work this way. But many others now rely on identity providers to reduce their development and maintenance burden and their users’ effort.
An identity provider creates, maintains, and manages identity information, and can provide authentication services to other applications. For example, Google Accounts is an identity provider. They store account information such as your user name, full name, job title, and email address. Slate online magazine lets you log in with Google (or another identity provider) rather than go through the steps of entering and storing your information anew.
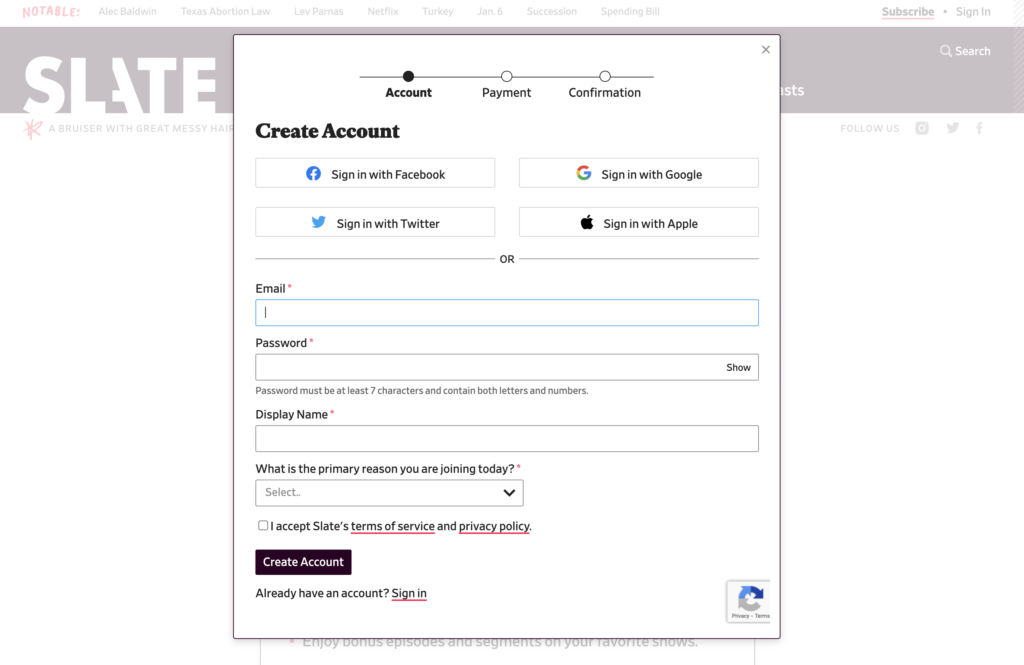
Identity providers don’t share your authentication credentials with the apps that rely on them. Slate, for example, doesn’t ever see your Google password. Google only lets Slate know that you’ve proven your identity.
Other identity providers include social media (such as Facebook or LinkedIn), enterprise (such as Microsoft Active Directory), and legal identity providers (such as Swedish Bank ID).
Authentication factors
Authentication factors are methods for proving a user’s identity. They commonly fall into these basic types:
IAM systems require one or many authentication factors to verify identity.
Authentication and authorization standards
Authentication and authorization standards are open specifications and protocols that provide guidance on how to:
- Design IAM systems to manage identity
- Move personal data securely
- Decide who can access resources
These IAM industry standards are considered the most secure, reliable, and practical to implement:
OAuth 2.0
OAuth 2.0 is a delegation protocol for accessing APIs and is the industry-standard protocol for IAM. An open authorization protocol, OAuth 2.0 lets an app access resources hosted by other web apps on behalf of a user without ever sharing the user’s credentials. It’s the standard that allows third-party developers to rely on large social platforms like Facebook, Google, and Twitter for login.
Open ID Connect
A simple identity layer that sits on top of OAuth 2.0, OpenID Connect (OIDC) makes it easy to verify a user’s identity and obtain basic profile information from the identity provider. OIDC is another open standard protocol.
JSON web tokens
JSON web tokens (JWTs) are an open standard that defines a compact and self-contained way for securely transmitting information between parties as a JSON object. JWTs can be verified and trusted because they’re digitally signed. They can be used to pass the identity of authenticated users between the identity provider and the service requesting the authentication. They also can be authenticated and encrypted. To learn more, read JSON Web Tokens.
Security Assertion Mark up Language (SAML)
Security Assertion Mark up Language (SAML) is an open-standard, XML-based data format that lets businesses communicate user authentication and authorization information to partner companies and enterprise applications that their employees use. To learn more, read SAML.
Web Services Federation (WS-Fed)
Developed by Microsoft and used extensively in their applications, this standard defines the way security tokens can be transported between different entities to exchange identity and authorization information.
Why use an IAM platform?
Why do so many developers choose to build on an identity and access management platform instead of building their own solution from the ground up?
User expectations, customer requirements, and compliance standards introduce significant technical challenges. With multiple user sources, authentication factors, and open industry standards, the amount of knowledge and work required to build a typical IAM system can be enormous. A strong IAM platform has built-in support for all identity providers and authentication factors, offers APIs for easy integration with your software, and relies on the most secure industry standards for authentication and authorization.
Benefits of IAM systems
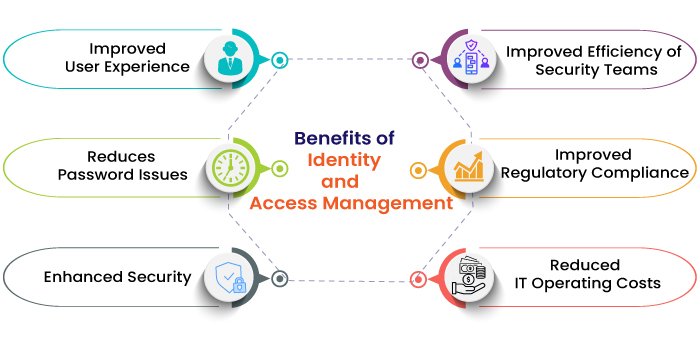
Implementing an Identity Management system provides a wide range of benefits to organizations, such as:
- Secure access: Opening networks to more employees, new contractors, customers, and partners offers greater efficiency and productivity, but it also increases the risk. An IAM solution enables businesses to extend access to their apps, networks, and systems on-premises and in the cloud without compromising security.
- Reduced help desk requests: An IAM solution removes the need for users to submit password resets and help desk requests by automating them. This enables users to quickly and easily verify their identity without bothering system admins, who in turn are able to focus on tasks that add greater business value.
- Reduced risk: Greater user access control means reduced risk of internal and external data breaches. This is vital as hackers increasingly target user credentials as a key method for gaining access to corporate networks and resources.
- Meeting compliance: An effective IAM system helps a business meet their compliance needs amid a landscape of increasingly stringent data and privacy regulations.
Basic components of IAM
IAM is a critical component of cybersecurity, ensuring that the right people have access to the right resources at the right time. The core components of IAM include:
1. Authentication
- Verifies the identity of a user.
- Involves:
- Username and password
- Biometrics (fingerprint, facial recognition)
- Tokens
- Multi-factor authentication (MFA)
2. Authorization
- Determines what a user can access once authenticated.
- Involves:
- Role-based access control (RBAC)
- Attribute-based access control (ABAC)
- Least privilege principle
- Access controls (read, write, execute)
3. User Management
- Manages user identities throughout their lifecycle.
- Involves:
- User provisioning and de-provisioning
- User profile management
- Group management
- Password management
4. Auditing and Reporting
- Tracks and records user activities.
- Involves:
- Log analysis
- Security incident and event management (SIEM)
- Compliance reporting
Additional Components
- Central User Repository: Stores user information and attributes.
- Single Sign-On (SSO): Allows users to access multiple applications with one set of credentials.
- Identity Governance and Administration (IGA): Manages user identities and access rights across the organization.
Best Practices for Identity and Access Management
Foundational Principles:
- Least Privilege: Grant users only the necessary permissions to perform their job functions.
- Separation of Duties: Distribute critical tasks across multiple individuals to prevent unauthorized access.
- Need-to-Know Access: Limit access to information based on job requirements.
- Regular Reviews: Conduct periodic audits of user access and permissions.
Specific Considerations:
- Cloud Environments: Leverage cloud-native IAM features and consider identity federation.
- Mobile Devices: Implement mobile device management (MDM) and mobile application management (MAM) solutions.
- Third-Party Applications: Manage access to third-party applications through IAM integrations.
Conclusion
Identity and Access Management (IAM) is no longer a luxury but a necessity in today’s digital landscape. It serves as the cornerstone of an organization’s security infrastructure, safeguarding sensitive data and systems from unauthorized access.
While IAM presents challenges, the benefits far outweigh the complexities. By adopting best practices, organizations can establish a robust IAM framework that protects their assets, mitigates risks, and supports business growth. In essence, IAM is not just about technology; it’s about safeguarding an organization’s most valuable assets: its data and reputation.
FAQs
Identity and Access Management (IAM) is a framework of policies, processes, and technologies that enable organizations to manage digital identities and control user access to critical corporate information.
By assigning users with specific roles and ensuring they have the right level of access to corporate resources and networks, IAM improves security and user experience, enables better business outcomes, and increases the viability of mobile and remote working and cloud adoption.
The core objective of an IAM platform is to assign one digital identity to each individual or a device. From there, the solution maintains, modifies, and monitors access levels and privileges through each user’s access life cycle.
