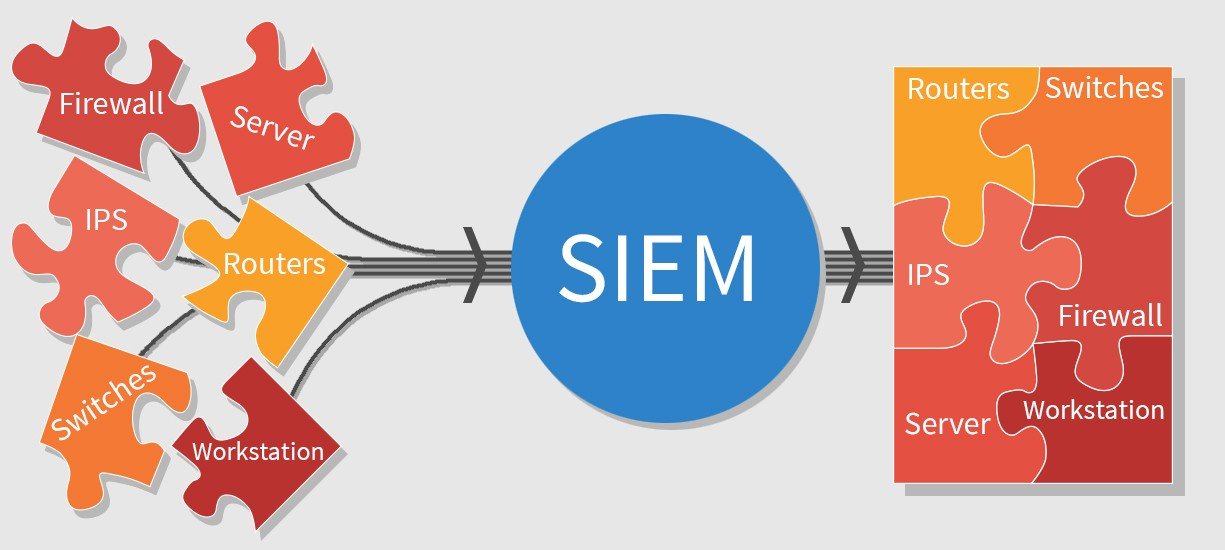
Security information and event management, SIEM for short, is a solution that helps organizations detect, analyse, and respond to security threats before they harm business operations.
SIEM, pronounced “sim,” combines both security information management (SIM) and security event management (SEM) into one security management system. SIEM technology collects event log data from a range of sources, identifies activity that deviates from the norm with real-time analysis, and takes appropriate action.
In short, SIEM gives organizations visibility into activity within their network so they can respond swiftly to potential cyberattacks and meet compliance requirements.
In the past decade, SIEM technology has evolved to make threat detection and incident response smarter and faster with artificial intelligence.
Why is SIEM important?
SIEM makes it easier for enterprises to manage security by filtering massive amounts of security data and prioritizing the security alerts the software generates.
SIEM software enables organizations to detect incidents that may otherwise go undetected. The software analyzes the log entries to identify signs of malicious activity. In addition, since the system gathers events from different sources across the network, it can re-create the timeline of an attack, enabling an organization to determine the nature of the attack and its effect on the business.
A SIEM system can also help an organization meet compliance requirements by automatically generating reports that include all the logged security events among these sources. Without SIEM software, the company would have to gather log data and compile the reports manually.
A SIEM system also enhances incident management by helping the company’s security team to uncover the route an attack takes across the network, identify the sources that were compromised and provide the automated tools to prevent the attacks in progress.
How does SIEM work?
SIEM tools gather event and log data created by host systems throughout a company’s infrastructure and bring that data together on a centralized platform. Host systems include applications, security devices, antivirus filters and firewalls. SIEM tools identify and sort the data into categories such as successful and failed logins, malware activity and other likely malicious activity.
The SIEM software generates security alerts when it identifies potential security issues. Using a set of predefined rules, organizations can set these alerts as a low or high priority.
For instance, a user account that generates 25 failed login attempts in 25 minutes could be flagged as suspicious but still be set at a lower priority because the login attempts were probably made by a user who had forgotten their login information.
Benefits of SIEM

Improved Threat Detection and Response
- Centralized Visibility: SIEM collects and correlates security data from various sources, providing a comprehensive view of the IT environment.
- Real-time Monitoring: It enables continuous monitoring of network activity, identifying potential threats as they emerge.
- Faster Incident Response: By automating threat detection and alerting, SIEM reduces response times to security incidents.
Enhanced Security Posture
- Risk Reduction: Proactive threat detection and response help mitigate risks to the organization.
- Compliance Adherence: SIEM assists in meeting regulatory requirements by providing audit trails and compliance reports.
- Data Loss Prevention: By monitoring data access and usage patterns, SIEM helps prevent data breaches.
Operational Efficiency
- Reduced Alert Fatigue: SIEM can filter and prioritize alerts, reducing the number of false positives.
- Automated Reporting: It generates customizable reports for compliance, security metrics, and incident investigations.
- Cost Savings: By streamlining security operations and reducing the impact of incidents, SIEM can lead to cost savings.
Additional Benefits
- Forensics and Investigation: SIEM provides valuable data for investigating security incidents and identifying attack vectors.
- Capacity Planning: By analysing log data, organizations can optimize resource allocation and capacity planning.
Limitations of SIEM
Despite its benefits, SIEM also has the following limitations:
- It can take a long time to implement SIEM because it requires support to ensure successful integration with an organization’s security controls and the many hosts in its infrastructure. It typically takes 90 days or more to install SIEM before it starts to work.
- It’s expensive. The initial investment in SIEM can be in the hundreds of thousands of dollars. And the associated costs can add up, including the costs of personnel to manage and monitor a SIEM implementation, annual support and software or agents to collect data.
- Analyzing, configuring and integrating reports require the talent of experts. That’s why some SIEM systems are managed directly within a security operations centre, a centralized unit staffed by an information security team that deals with an organization’s security issues.
- SIEM tools usually depend on rules to analyze all the recorded data. The problem is that a company’s network could generate thousands of alerts per day. It’s difficult to identify potential attacks because of the number of irrelevant logs.
- A misconfigured SIEM tool might miss important security events, making information risk management less effective.
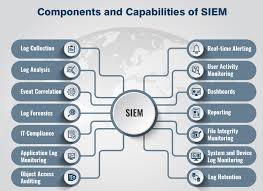
SIEM features and capabilities
Important features to consider when evaluating SIEM products include the following:
- Data aggregation. Data is collected and monitored from applications, networks, servers and databases.
- Correlation. Typically a part of SEM in a SIEM tool, correlation refers to the tool finding similar attributes between different events.
- Dashboards. Data is collected and aggregated from applications, databases, networks and servers and is displayed in charts to help find patterns and to avoid missing critical events.
- Alerting. If a security incident is detected, SIEM tools can notify users.
- Automation. Some SIEM software might also include automated functions, such as automated security incident analysis and automated incident responses.
Users should also ask the following questions about SIEM product capabilities:
- Integration with other controls. Can the system give commands to other enterprise security controls to prevent or stop attacks in progress?
- Artificial intelligence (AI). Can the system improve its own accuracy through machine learning and deep learning?
- Threat intelligence feeds. Can the system support threat intelligence feeds of the organization’s choosing, or is it mandated to use a particular feed?
- Extensive compliance reporting. Does the system include built-in reports for common compliance needs and provide the organization with the ability to customize or create new compliance reports?
- Forensic capabilities. Can the system capture additional information about security events by recording the headers and contents of packets of interest?
SIEM tools and software
There are a wide variety of SIEM tools on market, but the following is just a sample:
- Splunk. Splunk is an on-premises SIEM system that supports security monitoring and offers continuous security monitoring, advanced threat detection, incident investigation and incident response.
- IBM Q Radar. The IBM Q Radar SIEM platform provides security monitoring for IT infrastructures. It features log data collection, threat detection and event correlation.
- Log Rhythm is a SIEM system for smaller organizations. It unifies Log Management, network monitoring and endpoint monitoring, as well as forensics and security analytics.
- Ex abeam. Ex abeam Inc.’s SIEM portfolio offers a data lake, advanced analytics and a threat hunter.
- Net Witness. The RSA Net Witness platform is a threat detection and response tool that includes data acquisition, forwarding, storage and analysis.
- Data dog Cloud SIEM. Data dog Cloud SIEM from Data dog Security is a cloud-native network and management system. The tool features both real-time security monitoring and log management.
- Log360. The Log360 SIEM tool offers threat intelligence, incident management and SOAR features. Log collection, analysis, correlation, alerting and archiving features are available in real time.
- SolarWinds Security Event Manager. The SolarWinds Security Event Manager SIEM tool automatically detects threats, monitors security policies and protects networks. The tool offers features such as integrity monitoring, compliance reporting and centralized log collection.
How to choose the right SIEM product
The key to selecting the right SIEM tool varies depending on a number of factors, including an organization’s budget and security posture. However, companies should look for SIEM tools that offer the following capabilities:
- compliance reporting;
- incident response and forensics;
- database and server access monitoring;
- internal and external threat detection;
- real-time threat monitoring, correlation and analysis across a variety of applications and systems;
- an intrusion detection system, IPS, firewall, event application log, and other application and system integrations;
- threat intelligence; and
- user activity monitoring.
History of SIEM
SIEM technology, which has existed since the mid-2000s, initially evolved from log management, which is the collective processes and policies used to administer the generation, transmission, analysis, storage, archiving and disposal of large volumes of log data created within an information system.
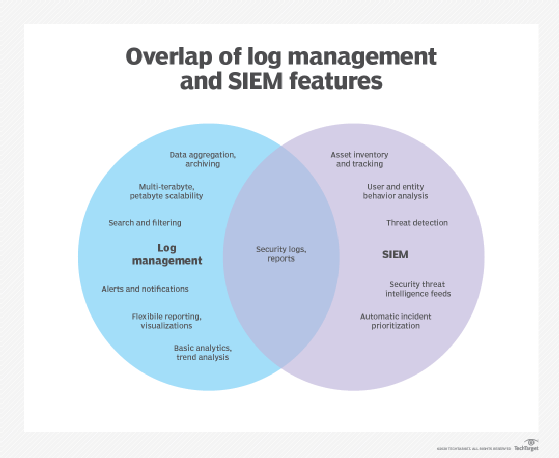
Gartner Inc. analysts coined the term SIEM in the 2005 Gartner report, “Improve IT Security with Vulnerability Management.” In the report, the analysts proposed a new security information system based on SIM and SEM.
Built on legacy log collection management systems, SIM introduced long-term storage analysis and reporting on log data. SIM also integrated logs with threat intelligence. SEM addressed identifying, collecting, monitoring and reporting security-related events in software, systems or IT infrastructure.
Vendors created SIEM by combining SEM, which analyzes log and event data in real time, providing threat monitoring, event correlation and incident response, with SIM, which collects, analyzes and reports on log data.
SIEM is now a more comprehensive and advanced tool. New tools were introduced for reducing risk in an organization, such as the use of machine learning and AI to help systems flag anomalies accurately. Eventually, SIEM products with these advanced features started being called next-generation SIEM.
The future of SIEM
Future SIEM trends include the following:
- Improved orchestration. Currently, SIEM only provides companies with basic workflow automation. However, as these organizations continue to grow, SIEM must offer additional capabilities. For example, with AI and machine learning, SIEM tools must offer faster orchestration to provide the different departments within a company the same level of protection. Additionally, the security protocols and the execution of those protocols will be faster, more effective and more efficient.
- Better collaboration with managed detection and response (MDR) tools. As threats of hacking and unauthorized access continue to increase, it’s important that organizations implement a two-tier approach to detect and analyze security threats. A company’s IT team can implement SIEM in-house, while a managed service provider can implement the MDR tool.
- Enhanced cloud management and monitoring. SIEM vendors will improve the cloud management and monitoring capabilities of their tools to better meet the security needs of organizations that use the cloud.
- SIEM and SOAR will evolve into one tool. Look for traditional SIEM products to take on the benefits of SOAR; however, SOAR vendors will likely respond by expanding the capabilities of their products.
Use cases
Computer security researcher identified the following SIEM use cases, presented at the hacking conference 28C3 (Chaos Communication Congress).
- SIEM visibility and anomaly detection could help detect zero-days or polymorphic code. Primarily due to low rates of anti-virus detection against this type of rapidly changing malware.
- Parsing, log normalization and categorization can occur automatically, regardless of the type of computer or network device, as long as it can send a log.
- Visualization with a SIEM using security events and log failures can aid in pattern detection.
- Protocol anomalies that can indicate a misconfiguration or a security issue can be identified with a SIEM using pattern detection, alerting, baseline and dashboards.
- SIEMS can detect covert, malicious communications and encrypted channels.
- Cyberwarfare can be detected by SIEMs with accuracy, discovering both attackers and victims.
Correlation rules examples
SIEM systems can have hundreds and thousands of correlation rules. Some of these are simple, and some are more complex. Once a correlation rule is triggered the system can take appropriate steps to mitigate a cyber attack. Usually, this includes sending a notification to a user and then possibly limiting or even shutting down the system.
Impossible Travel
When a user logs in to a system, generally speaking, it creates a timestamp of the event. Alongside the time, the system may often record other useful information such as the device used, physical location, IP address, incorrect login attempts, etc. The more data is collected the more use can be gathered from it. For impossible travel, the system looks at the current and last login date/time and the difference between the recorded distances. If it deems it’s not possible for this to happen, for example traveling hundreds of miles within a minute, then it will set off a warning.
Many employees and users are now using VPN services which may obscure physical location. This should be taken into consideration when setting up such a rule.
Excessive File Copying
The average user does not typically copy or move files on the system repeatedly. Thus, any excessive file copying on a system could be attributed to an attacker wanting to cause harm to an organization. Unfortunately, it’s not as simple as stating someone has gained access to your network illegally and wants to steal confidential information. It could also be an employee looking to sell company information, or they could just want to take home some files for the weekend.
DDoS Attack
A DDoS (Distributed Denial of Service) Attack could cause significant damage to a company or organization. A DDoS attack can not only take a website offline, it can also make a system weaker. With suitable correlation rules in place, a SIEM should trigger an alert at the start of the attack so that the company can take the necessary precautionary measures to protect vital systems.
File Integrity Change
File Integrity and Change Monitoring (FIM) is the process of monitoring the files on your system. Unexpected changes in your system files will trigger an alert as it’s a likely indication of a cyber attack.
Challenges of traditional SIEM

Organizations using legacy security information and event management solutions to manage data security operations and the incident response process may often grapple with the following limitations:
- Hassles in Data Collection and Correlation: Traditional SIEM security solutions can struggle to collect large volumes of data from multiple sources seamlessly. Manual data correlation can also be a complicated and time-consuming task.
- Growing Costs: The total cost of ownership (TCO) for setting up and maintaining legacy SIEM systems can be a burden for an organization. With growing data volumes, the overheads, including personnel cost, maintenance, and support charges, can rise, and organizations may experience limited value at higher costs.
- Complex Manual Investigation: Lack of automation can hinder the detailed analysis of extensive data. Manual log management and event correlation can also result in irrelevant information, further complicating threat identification and analysis.
- Delayed Response: Time is of the essence when managing and monitoring threat environments. Delay in prioritizing high-risk activities and lack of real-time monitoring can restrict IT security teams from proactively identifying potential security threats and mitigating the affects.
Threats Associated with SIEM
While SIEM is a powerful tool for enhancing security, it’s essential to acknowledge its potential drawbacks and challenges:
1. Data Overload and False Positives:
- Massive Data Volume: SIEM systems collect vast amounts of data, which can overwhelm analysts and lead to alert fatigue.
- False Positives: Overly sensitive rules can generate numerous false alarms, wasting analyst time and resources.
2. Complexity and Skill Requirement:
- Steep Learning Curve: Implementing and managing a SIEM requires specialized skills and expertise.
- Configuration Challenges: Configuring rules and correlations effectively can be complex and time-consuming.
3. Cost and Resource Intensive:
- High Initial Investment: SIEM solutions can be expensive to purchase, implement, and maintain.
- Ongoing Operational Costs: Staff training, hardware, software, and licensing costs are ongoing expenses.
4. Dependency on Data Quality:
- Inaccurate or Incomplete Data: The effectiveness of SIEM relies on high-quality data from various sources.
- Data Loss or Corruption: Data loss or corruption can hinder threat detection and incident response.
5. Potential for Evasion:
- Advanced Threats: Sophisticated attackers can find ways to bypass SIEM detection mechanisms.
- Insider Threats: Malicious insiders can manipulate SIEM data or configurations to avoid detection.
6. Scalability Challenges:
- Growth and Expansion: As organizations grow, SIEM systems may struggle to handle increased data volume and complexity.
- Performance Issues: Scalability issues can impact SIEM performance and effectiveness.
7. Privacy Concerns:
- Sensitive Data: SIEM collects and stores sensitive information, which requires robust data protection measures.
- Compliance Risks: Improper handling of personal data can lead to compliance violations.
Solutions of SIEM
Addressing the challenges of SIEM requires a comprehensive approach involving technology, processes, and people.
Technological Solutions
- Data Reduction and Normalization: Implement techniques like data deduplication, compression, and normalization to manage data volume.
- Advanced Analytics: Utilize machine learning and artificial intelligence to identify patterns and anomalies, reducing false positives.
- SOAR Integration: Combine SIEM with Security Orchestration, Automation, and Response (SOAR) to automate incident response processes.
- Threat Intelligence Integration: Incorporate threat intelligence feeds to prioritize alerts and improve detection accuracy.
Process-Oriented Solutions
- Incident Response Plan: Develop and regularly test an incident response plan to streamline response efforts.
- Role-Based Access Control: Implement strict access controls to protect sensitive SIEM data and prevent unauthorized access.
- Regular Tuning: Continuously monitor and fine-tune SIEM rules and alerts to optimize performance and reduce false positives.
- Data Retention Policies: Establish clear data retention policies to balance security needs with storage costs.
People-Centric Solutions
- Skilled Workforce: Invest in training and development to build a skilled SIEM team.
- Clear Roles and Responsibilities: Define clear roles and responsibilities within the security team.
- Incident Response Drills: Conduct regular incident response drills to improve team coordination and efficiency.
- Continuous Learning: Encourage a culture of continuous learning and knowledge sharing.
Additional Considerations
- Hybrid SIEM: Consider a hybrid approach combining on-premises and cloud-based SIEM components.
- SIEM as a Service (SIaaS): Explore SIEM as a service options to reduce upfront costs and management overhead.
- Vendor Selection: Carefully evaluate SIEM vendors based on features, scalability, pricing, and support.
Best practices to implementing SIEM

Follow these best practices while implementing SIEM:
- Set understandable goals. The SIEM tool should be chosen and implemented based on security goals, compliance and the potential threat landscape of the organization.
- Apply data correlation rules. Data correlation rules should be implemented across all systems, networks and cloud deployments so data with errors in it can be more easily found.
- Identify compliance requirements. This helps ensure the chosen SIEM software is configured to audit and report on correct compliance standards.
- List digital assets. Listing all digitally stored data across an IT infrastructure aids in managing log data and monitoring network activity.
- Record incident response plans and workflows. This helps ensure teams can respond to security incidents rapidly.
- Assign a SIEM administrator. A SIEM administrator ensures the proper maintenance of a SIEM implementation.
Conclusion
In conclusion, SIEM is not merely a technology but a critical component of a robust security strategy. By investing in a well-implemented SIEM solution and fostering a culture of security awareness, organizations can significantly enhance their resilience against cyber threats and safeguard their valuable assets.
SIEM (Security Information and Event Management) has evolved into an indispensable tool for modern organizations navigating the complex cybersecurity landscape. By centralizing log management, correlating events, and providing real-time insights, SIEM empowers businesses.
While SIEM presents challenges such as data overload and complexity, these can be effectively addressed through strategic planning, skilled personnel, and advanced technologies. The integration of SIEM with other security solutions like SOAR and threat intelligence platforms further amplifies its effectiveness.
FAQs
SIEM solutions collect logs and analyze security events along with other data to speed threat detection and support security incident and event management, as well as compliance.
SIEM technology gathers security-related information from servers, end-user devices, networking equipment, and applications, as well as security devices.
SIEM solutions provide key threat-detection capabilities, real-time reporting, compliance tools, and long-term log analysis.