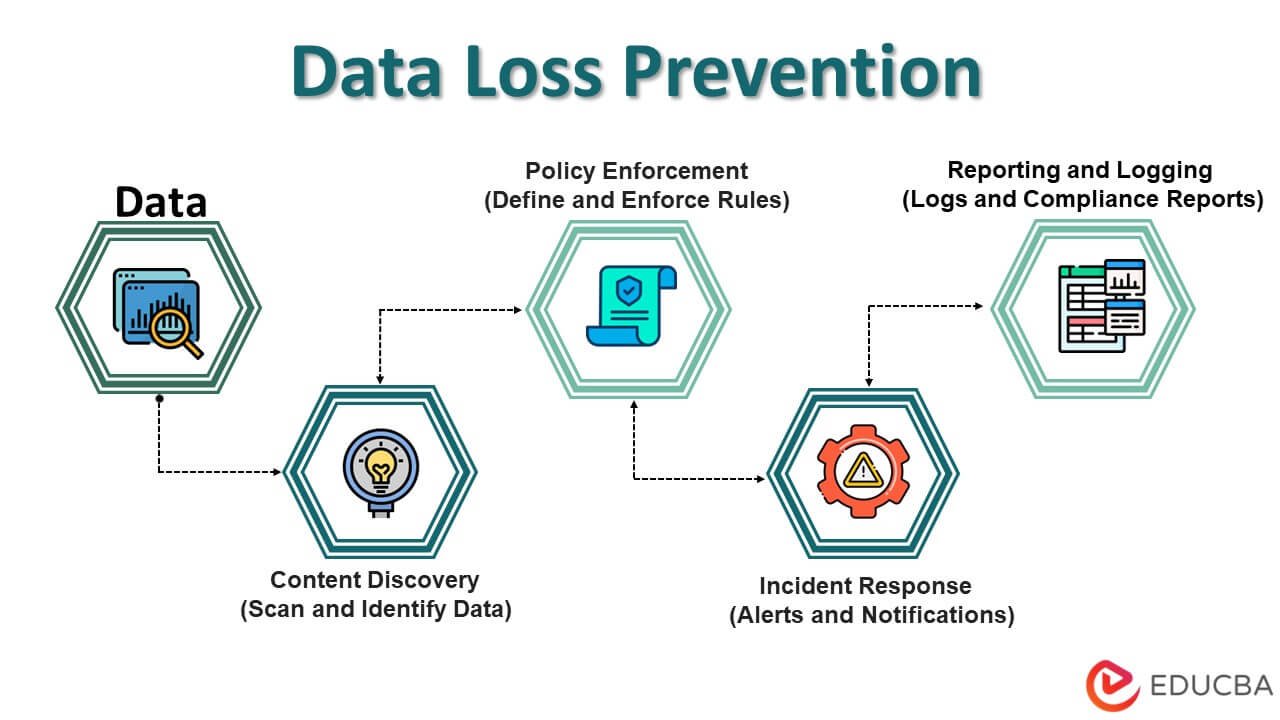
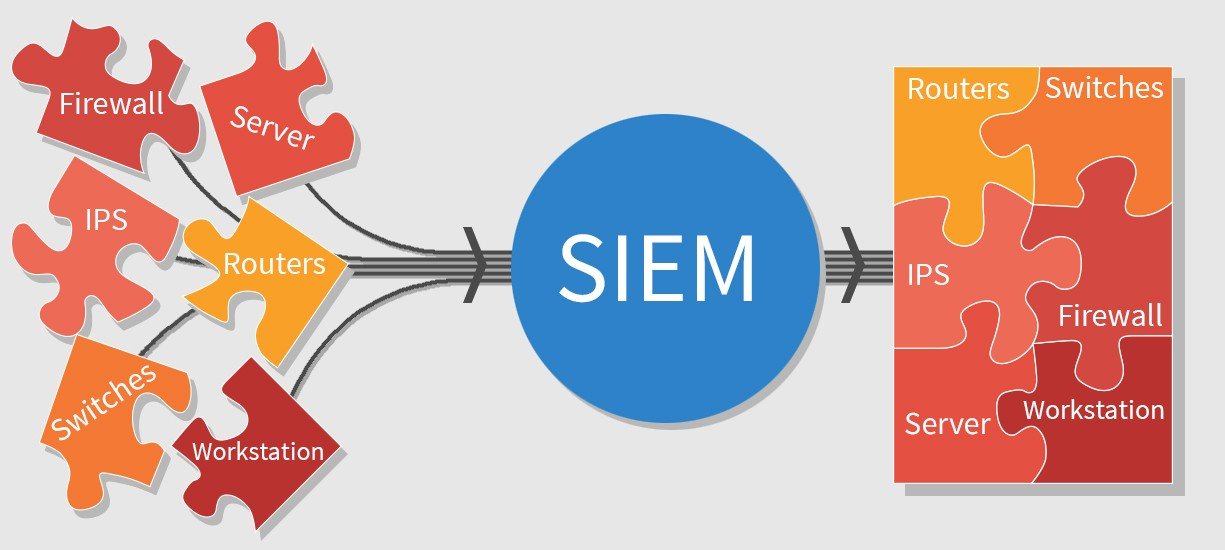
Incident Response
Incident response is the strategic, organized response an organization uses following a cyberattack. The response is executed according to planned procedures that seek to limit damage and repair breached vulnerabilities in systems. IT professionals use incident response plans to manage security incidents. Having a clearly defined incident response plan can limit attack damage, lower costs, and save … Read more